The 30 Hottest New Cybersecurity Tools Announced At RSA Conference 2020
From behavior profiling of IoT devices to container-based isolation for key applications to eliminating spoofing links in emails, here's a look at 30 key cybersecurity tools unveiled at the RSA Conference this year.

Leading The Way In Security
Vendors are taking advantage of RSA Conference 2020's bright spotlight to launch new offerings, features, platforms and tools that will define the industry for months and years to come. For the more than 700 exhibitors typically found at RSA, the gathering provides an opportunity to promote new products and highlight shifts in strategy to an audience of more than 42,500.
Some of the more common areas for product innovation this year include application security, cloud security, email security and IoT security. CRN broke out the three of the most popular areas for new product development—identity and data protection, endpoint and network security, and risk, operations and threat intelligence—into their own stand-alone slide shows.
From accelerating the patching of vulnerabilities to behavior profiling for enterprise IoT devices to container-based isolation for core applications to minimizing the risk of spoofing links in emails, here's a look at 30 key cybersecurity tools announced at RSA Conference 2020.
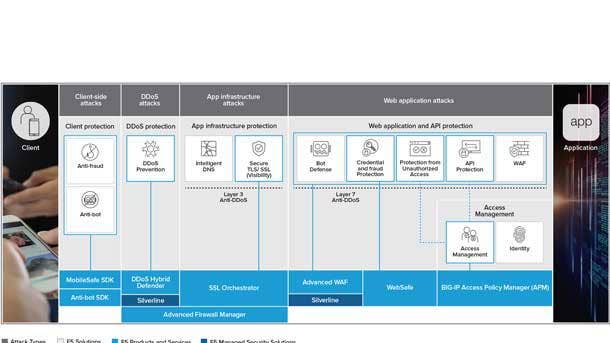
F5 Application Protection
F5’s Application Protection portfolio safeguards all applications without impacting the user experience or impeding the delivery of digital services from code to customer, the company said. The company said it has realized operational efficiencies by seamlessly enabling application security across multiple environments with consistent policies and controls.
F5 said its offerings guard against application threats such as application-layer denial of service, malicious scripting and injection attacks, with Shape Enterprise Defense mitigating attacks tied to app fraud and abuse. And the F5 identity-aware proxy enables single sign-on and multi-actor authentication policies to help organizations realize the benefits of modern authentication and authorization protocols.
The company also offers a managed service focused on DDoS through Silverline to help protect customers from volumetric or reflected amplification attacks. From there, F5’s intelligent threat services use advanced analytics to transform the data sets into tactical intelligence that is both relevant and consumable by portfolio services.

CrowdStrike Endpoint Recovery Services
CrowdStrike Endpoint Recovery Services combines the power of the CrowdStrike Falcon platform, threat intelligence and real-time response to accelerate business recovery from cyber intrusions, the company said. The new service enables customers to rapidly mitigate security incidents and resume business operations with minimal interruptions, according to CrowdStrike.
CrowdStrike said Endpoint Recovery Services accelerates the standard life cycle of incident recovery, saving businesses from expensive downtime. Endpoint Recovery Services combines CrowdStrike Falcon, endpoint visibility from Threat Graph and experienced security analysts to ensure immediate attack disruption and comprehensive endpoint remediation, according to the company.
Endpoint Recovery Services stops attacks to minimize downtime and restores business operations without having to reimage or reissue endpoint devices, enabling customers to focus on recovering other critical business components. The initial phases of the service are focused on understanding the incident and deploying the Falcon platform without the need for on-premises visits or installations.
Proofpoint BEC/EAC Integrated Solution
Proofpoint has debuted the first offering to address both business email compromise (BEC) and email account compromise (EAC) attacks by combining the company’s secure email gateway, advanced threat protection, threat response, email authentication, security awareness training, and cloud account protection.
Stopping BEC and EAC attacks is top of mind for organizations as cybercriminals continue targeting individuals via email with highly personalized social engineering messages, Proofpoint said. These messages can take the form of BEC imposter emails that work to trick people into sending money and data to fake accounts and recipients, according to Proofpoint.
In the case of EAC, Proofpoint said fraudsters work to compromise email accounts via credential phishing, password spraying, and/or malicious third-party applications to maintain persistence. Armed with insight into business operations, Proofpoint said the attackers can craft and send convincing and timely emails masquerading as a real employee with what appears to be a legitimate financial request.
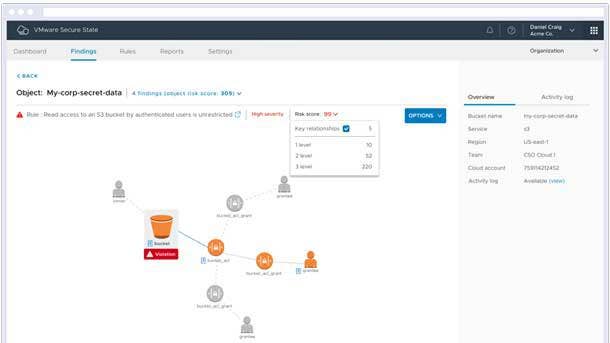
VMware Secure State
VMware Secure State’s real-time detection and remediation capabilities make it possible for customers to close the loop on cloud security and mitigate risks proactively, the company said. The new flexible remediation framework is designed to help cloud security teams collaborate with DevOps teams and gain trust as they gradually scale best practices, according to VMware.
The new VMware Secure State service provides predefined, out-of-the-box actions as well as the ability to create new custom actions as code, the company said. In addition, VMware said all actions can be targeted to selectively remediate resources based on conditions such as cloud accounts, regions or resource tags.
To address existing misconfigurations, VMware said security teams can either bulk-remediate violations themselves or publish actions to delegate decisions to DevOps teams. And to prevent new misconfigurations, VMware said customers can build guardrails that auto-remediate violations at real-time speed.
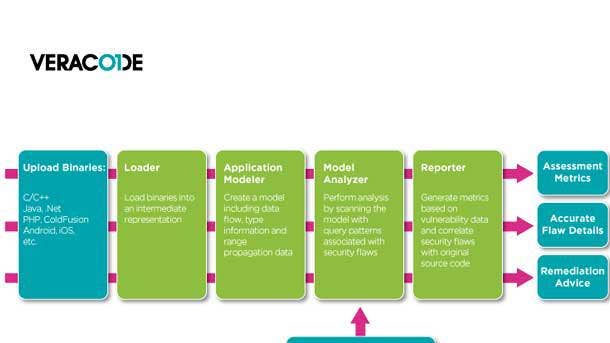
Veracode Static Analysis
A new release of Veracode Static Analysis features comprehensive analysis across the development life cycle, including a new Pipeline Scan that is optimized for use when code is submitted to the build process. The offering meets the needs of DevSecOps programs with three scan types delivering fast, accurate results at all stages of the development life cycle, according to Veracode.
Veracode Static Analysis is a DevSecOps tool for organizations that innovate through software and need to deliver code on time, the company said. IDE Scan allows developers to discover flaws pre-commit in real-time as they write code, which will help catch issues while they are easier and less expensive to fix.
From there, Veracode said the new Pipeline Scan helps developers address security flaws quickly in the pipeline by providing fast feedback on every build in a continuous integration environment. And prior to releasing software, Veracode said Policy Scan completes a full assessment of the code with an audit trail for management and compliance purposes.
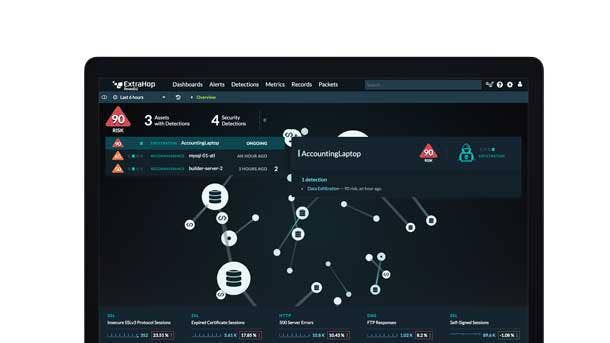
ExtraHop Reveal(x)
ExtraHop Reveal(x) now provides advanced discovery, classification and behavior profiling for enterprise IoT devices, providing visibility from the device to the service layer, the company said. The latest enhancements extend Reveal(x) capabilities to the enterprise IoT device edge, providing complete visibility, detection and response across the attack surface without the need for point products.
With the latest release, ExtraHop Reveal(x) can discover, identify and profile all IoT devices and services to deliver complete visibility without friction to IT and Security Operations teams. From there, device behavior profiling extracts rich data from network and cloud traffic, which ExtraHop said enables deeper analysis across devices at the service level.
Meanwhile, guided investigation automatically gathers contextual information, related decisions and packet level details into a single workflow, enabling security analysts and threat hunters to quickly determine the impact and scope of an IoT event. And IoT security hygiene address issues like IoT devices and services using unencrypted communications, and is capable of isolating devices in the network.
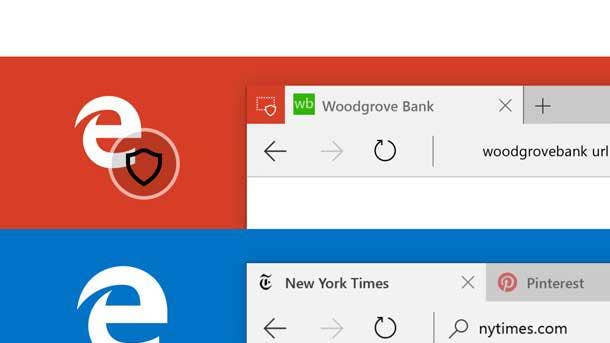
Microsoft Application Guard
Microsoft’s integration of Application Guard with Office 365 ProPlus provides an upgrade to protected view that helps desktop users stay safer and more proactive with container-based isolation for Office applications. Application Guard’s enforcement completely blocks access to memory, local storage, installed applications, corporate network endpoints or any other resources of interest to the attacker.
As a result, Microsoft said Office users will be able to open an untrusted Word, Excel or PowerPoint file in a virtualized container, meaning that users can stay productive all while protected with hardware-level security. If the untrusted file is malicious, Microsoft said the attack is contained while user data and identity remain untouched.
And when a user wants to trust a document to save on the network or start collaborating in real time, Microsoft said Safe Documents will first check to help ensure the document is safe. Application Guard connects to the Microsoft Security Center, providing admins with advanced visibility and response capabilities including alerts, logs and confirmation the attack was contained, according to Microsoft.

Secureworks Cloud Configuration Review
Secureworks Cloud Configuration Review will help customers detect configuration vulnerabilities, understand the business impact of critical risks, and address the security and compliance challenges associated with public cloud adoption. A partnership with VMware will help address big cloud security challenges, including the exposure of critical assets due to misconfigurations and insider mistakes.
The service includes a customer workshop to understand a customer’s business context, multicloud footprint, security policies and compliance needs. From there, Secureworks said a scan of Amazon Web Services and Microsoft Azure infrastructure with VMware Secure State technology assesses cloud configurations against proprietary best practice and regulatory compliance frameworks.
A review of VMware’s findings by Secureworks can provide customers with a visual understanding of security risks, recommendations for remediation action, and guidance on how to prioritize security controls. Customers will receive 30-day access to VMware Secure State to improve understanding of cloud asset relationships and plan a remediation strategy in collaboration with other teams.
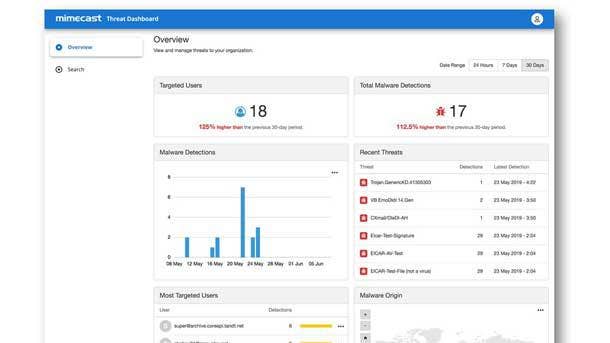
Mimecast Email Security 3.0
Mimecast’s Email Security 3.0 strategy helps organizations address threats at three distinct zones: at the email perimeter; inside the organization or network; and beyond the perimeter. The company has incorporated new major platform innovations to increase efficacy including web browser isolation, security awareness training integrations, and brand exploitation protection offerings, Mimecast said.
Mimecast Browser Isolation is designed to mitigate the risk of emails containing links to spoofed sites by preventing a direct connection between the user’s browser on their device and the target web page. Users are protected from potentially malicious action like the challenge of credential harvesting or malicious downloads as the browsing session is executed and contained within the Mimecast cloud.
In addition, Mimecast Awareness Training is fully integrated into the company’s cloud-based platform to make it easier for customers to administer awareness training into their broader security ecosystem. Plus, Mimecast Brand Exploit Protect runs targeted scans that identify unknown attack patterns, blocking compromised assets before they become live attacks as the earliest preparation stages.

Sectigo Web Security Platform
The Sectigo Web Security Platform helps customers easily identify threats and quickly patch vulnerabilities from an all-new comprehensive management portal. Through the platform, customers can automate daily scanning for vulnerabilities, receive proactive notifications, and instantly remove the malware found within the code, database, or files on the web server.
The platform also automates daily website backups so that customers can restore their sites when needed with a single click, according to Sectigo. Coming in future releases of the Sectigo Web Security Platform will be advanced features to accelerate website performance with a global content delivery network and domain name system, as well as to increase protection with a web application firewall.
Included in the Sectigo Web Security Platform is Sectigo Web Detect, which automatically scans up to five website pages once daily for issues such as malicious infections, spam listings, vulnerabilities and blacklisting. Meanwhile, Sectigo Web Patch scans daily to automatically detect critical weaknesses found in the company’s content management system or database and proactively patches the vulnerabilities.
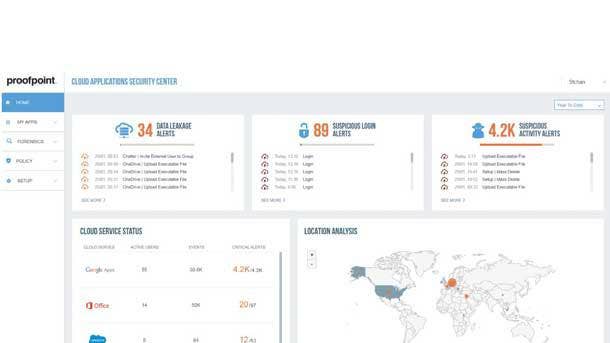
Proofpoint CASB
Innovations to the Proofpoint Cloud Access Security Broker (CASB) will help safeguard the cloud applications employees access every day, such as Amazon Web Services, Box, Google G Suite, Microsoft Office 365 and Slack. The offering gives organizations visibility and control over cloud applications while allowing security teams to deploy cloud services with confidence, Proofpoint said.
Proofpoint CASB now offers automated detection and remediation of malicious third-party applications in Microsoft Office 365 and Google G suite. This innovation will help stop attacks that may start by email and launch third-party applications that provide attackers with persistent system permissions and access, according to Proofpoint.
Risk-based access enhancements will detect if a user device is unmanaged and restricting access, Proofpoint said, plus users will be able to determine risk levels during login and respond with adaptive controls, such as multifactor authentication. And an integration with Proofpoint threat intelligence with expand suspicious file activity detection for Microsoft Office 365.

Nozomi Networks Version 20.0
Nozomi Networks Version 20.0 includes new groundbreaking anomaly detection technology that delivers unmatched accuracy for enterprise IoT networks. Customers also now have the option of centralizing the monitoring of distributed sites via a single console that can be deployed on the Microsoft Azure cloud platform, according to the company.
A new asset intelligence service in Nozomi Networks Version 20.0 continuously updates the adaptive learning technology with OT and IoT device information to significantly improve the accuracy of alerts in constantly changing IoT environments. The latest release also allows for the deployment of the cloud management console in Microsoft Azure, allowing for centralized management of decentralized assets.
Nozomi Networks 20.0 delivers fast-performing appliances designed to meet the large-scale and high-speed requirements of today’s converged OT, IoT and IT networks, the company said. The latest release also includes new and improved reports designed to give enterprise customers a better understanding of their converged IT/OT network and the risks they face, according to the company.
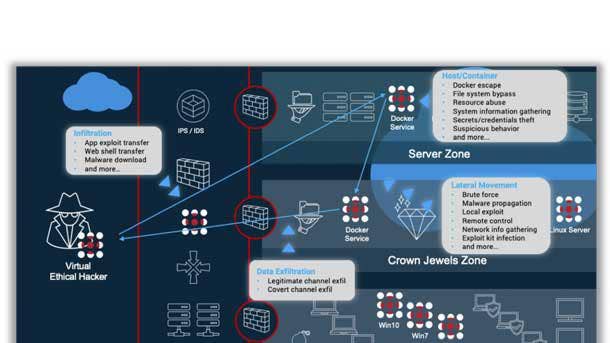
SafeBreach Cloud Native Container Security
The new Cloud Native Container Security capabilities of SafeBreach extend full breach-and-attack simulation coverage via a new Docker simulator to teams managing container-based infrastructures deploying Docker. These teams increasingly play a role in the security stance where modern DevOps practices use Continuous Integration/Continuous Deployment to rapidly iterate and ship new code.
SafeBreach simulates a growing list of attacks against the Docker data plane, network and API, including attacks involving process injection; rogue applications, system changes, and lateral movement from container to container.
SafeBreach is designed to empower SecOps teams to optimize their controls and configurations on a continuous basis to ensure all networks and hosts are as secure as possible. The breach-and-attack simulator makes it simple for users to simulate attacks customized to match any infrastructure footprint, visualize weakness in their security controls, and holistically remediate gaps and vulnerabilities.

Trustifi Optical Character Recognition Scan
The Trustifi Optical Character Recognition (OCR) tool scans email attachments such as images and PDF files, recognizing elements of a scan such as a credit card or a screenshot of a financial statement and categorizing those attachments as sensitive. It then automatically encrypts the attachment, reducing the opportunity for employees/individuals to mistakenly transmit confidential material unprotected.
This new OCR capability improves security for organizations that typically send classified, sensitive or personally identifying data via email, especially in verticals such as health care, retail and financial services, according to Trustifi. The OCR scan is useful in thwarting instances of phishing, which Trustifi said is one of the most common ways that hackers infiltrate commercial data stores.
Trustifi’s OCR feature leverages artificial intelligence and machine learning, building an ongoing base of images to be flagged and encrypted, according to the company. The OCR tool leverages character recognition to identify and automatically protect sensitive material the sender might not otherwise think twice about, Trustifi said.
CrowdStrike Falcon Cloud Workload Protection
CrowdStrike Falcon’s visibility has been expanded to protect workloads across all environments, including workloads and containers running in the cloud and in private, public and hybrid data centers or on-premises. Falcon is extending its endpoint detection and response capabilities to provide visibility specific to Google Cloud Platform and Microsoft Azure and provide run-time protection for containers.
Falcon Discover for Google Cloud Platform and Azure simplifies the process for organizations running workloads on either cloud, gathering up-to-date information and offering visibility into the scope and nature of their cloud footprint. It provides current information about workloads, including metadata about system size and configuration, networking and security information.
Falcon can additionally detect potential threats within containers in real time, leveraging advanced AI and machine learning to ensure security teams respond to these quickly to close security gaps left exposed within DevOps environments. Meanwhile, CrowdStrike said it’s extending its usage-based metered billing for customers running in both Google Cloud Platform and Azure cloud workloads.
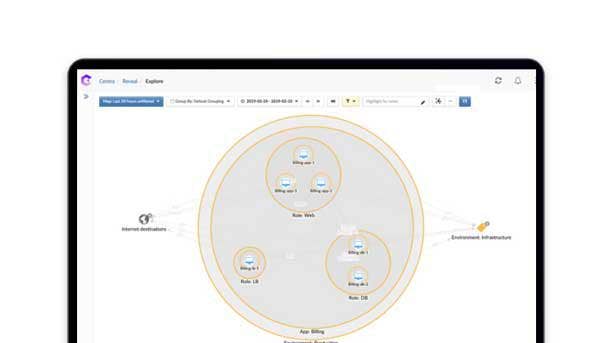
Guardicore Centra Security Platform
New Guardicore Centra Security Platform capabilities will help security architects visualize, segment, and protect cloud-native applications while further simplifying the process for reducing risk to mission-critical business applications through segmentation. Guardicore said it now protects cloud-native applications, including serverless computing and Platform as a Service (PaaS).
The platform enables IT security teams to visualize access to PaaS services by user, system or cloud service, providing a visual map of all interactions between those services, including application flows. Guardicore segmentation policies then control access to cloud resources to ensure only sanctioned users and systems are allowed, blocking unauthorized access and reducing the attack surface.
Meanwhile, Guardicore Centra’s AI-powered segmentation makes asset classification even easier and reduces the time and effort needed to apply a segmentation policy to new or existing applications. The platform provides asset classification and policy assistance around scoping and classifying applications, automatic prioritization recommendations, and automatic segmentation policy recommendations.

FireEye Messaging Security
FireEye Messaging Security protects collaboration tools such as Microsoft Teams and Slack, the company said. The new offering reduces the risk of a cyberattack by scanning objects and links shared via Slack or Teams, identifying zero-day malware and phishing links in real time.
Should a suspicious object be identified, the user will be alerted by FireEye Messaging Security, helping to keep the threat from extending to cloud file-sharing services. FireEye said the Messaging Security offering is part of its ongoing commitment to expanding protection around new collaboration tools.
Services such as Microsoft Teams and Slack have witnessed widespread adoption, according to FireEye, helping organizations achieve new heights in employee productivity. However, FireEye said this rapid growth has not gone unnoticed by attackers looking to weaponize new cloud-based tools to deliver malicious content.

eSentire esCloud
eSentire’s new esCloud portfolio brings around-the-clock configuration and vulnerability monitoring as well as threat detection and response to Infrastructure as a Service and Software as a Service. The portfolio extends eSentire’s managed detection and response (MDR) capabilities and threat hunting expertise from on-premises to modern cloud environments.
The esCloud portfolio will be generally available at the end of March and include support for Amazon Web Services, Microsoft Azure, Google Cloud Platform and Microsoft Office 365 from the get-go, with support for Google G Suite, Salesforce, ServiceNow, Dropbox and Box to follow later this year.
EsCloud constantly monitors customer cloud environments to detect improper configurations and vulnerabilities that could lead to data loss and compromise, according to eSentire. Automated policy enforcement, combined with response and remediation from eSentire’s expert security analysts, ensures that customers can operate in the cloud with confidence, the company said.
Humio Bucket Storage
Humio Bucket Storage is expected to make cloud deployments less expensive, faster and easier to run by using bucket storage for retaining data, the company said. The significant decrease in the cost of storage and infinite capacity removes concerns related to storing large volumes of data for a longer period of time, thereby enabling cloud scalability for organizations of all sizes, according to Humio.
Humio said it supports bucket storage designed for streaming data from all major cloud providers, as well as on-premises providers including Min.io. As a result, customers searching for retained data— even from years ago—can achieve results in seconds without reingesting, according to the company.
Bucket Storage enables infinite retention for storing more events than was practical with local disks, according to the company.

BluBracket Code Security Suite
The BluBracket Code Security Suite represents a comprehensive security offering for code in the enterprise, the company said. Its BluBracket:CodeInsights and BluBracket:CodeSecure products give companies what they need to unlock software innovation while protecting their enterprise infrastructure and valuable intellectual property, according to the company.
With BluBracket, companies can understand where their code is and who has access to it, classifying their most critical code for detailed chain of custody information for any compliance or audit needs. The company said it can also detect secrets in code, misconfiguration and other risks to ensure that no sensitive passwords or tokens are being misappropriated, mishandled or misused.
BluBracket said it offers all the visibility, alerting and remediation needed to act and protect code investment from both insider and outsider code threat or unauthorizing publishing to open source. Ultimately, BluBracket said it wishes to bridge the gap between the security, development and DevOps teams, making security policies actionable and enforceable in a continuous development pipeline.

beSecure-OT
BeSecure-OT is a complete vulnerability assessment and asset tracking offering for OT networks, delivering the information needed to repair the vulnerabilities that are most likely to cause data loss. The tool will map and score a company’s network to show in real time which network components are most vulnerable to attack and where to direct remediation resources to efficiently secure a network.
BeSecure-OT scans everything that “talks IP” automatically such as severs, industrial control systems, infrastructure, workstations, endpoints of any type, printers and IoT. It tests the behavior of OT devices by recording their responses to carefully crafted queries and is designed specifically for auditing OT networks and tracking their security over time.
The tool’s standard reports provide a comprehensive analysis of all vulnerabilities found grouped by risk severity or by most severely compromised asset. Every report contains technical information specific to the risk discovered, including a summary, a look at severity and possible impact, recommended solutions, and relevant information such as links to software vendor patches.
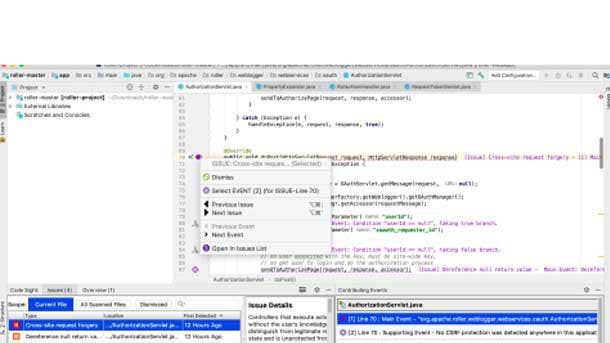
Synopsys Code Sight IDE
New Polaris capabilities combine software composition analysis (SCA) and static application security testing (SAST) in the interactive development environment (IDE), enabling developers to proactively find and fix security risks across third-party and custom components. This release allows for analysis of declared and transitive open-source dependencies, flagging components with known security issues.
With the new SCA capabilities, Synopsys said developers can review known vulnerabilities of flagged components to verify the risk and determine remediation options all without leaving the Code Sight IDE plugin. The Code Sight plugin provides vulnerability information from Black Duck Security Advisories, as well as public CVE records from the National Vulnerability Database.
The Code Sight plugin also helps developers quickly identify and select the best fix for vulnerabilities by providing detailed remediation guidance, directing them to secure more component versions. Along with vulnerability information, the Code Sight plugin provides open-source license risks and potential security and license compliance violations of the organization’s predefined open-source policies.
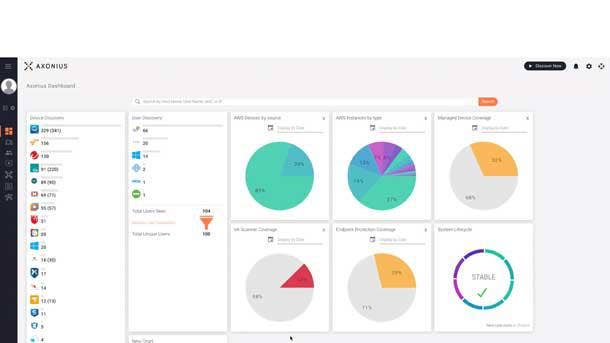
Axonius Cloud Asset Compliance
Axonius Cloud Asset Compliance leverages data aggregated from public cloud providers to automatically determine how cloud workload, configuration details, and accounts comply with the industry security benchmarks. The product automatically shows how each public cloud instance conforms to widely accepted security benchmarks as well as the organization’s overall security policy.
The product provides additional value in helping security and IT teams move fast by ensuring their cloud assets are secured as expected, along with offering detailed guidance on what to do any time an instance is no longer in compliance. The Axonius Cloud Asset Compliance add-on for AWS is already installed in customer environments and is available to try now, according to the company.
Axonius said it’s committed to showing customers what assets they have and whether those assets meet the security policy regardless of if the customers’ assets are devices on networks or instances in the cloud. From there, Axonius said it can help customers remediate issues as quickly or automatically as they want.

PreEmptive JSDefender
PreEmptive JSDefender is a tool used by software developers to protect JavaScript code from hacking, reverse engineering, and IP and data theft. It is PreEmptive’s first product offering in the JavaScript space, and it protects JavaScript using a variety of code obfuscation techniques and active runtime checks.
JSDefender works with all types of JavaScript code regardless of if it’s browser-based, mobile, desktop or server. It also supports TypeScript and integrates with popular bundling tools like webpack, according to PreEmptive.
Given the popularity of JavaScript and its usage in untrusted environments, PreEmptive said it wanted to help customers protect the value of their intellectual property and secure the sensitive data passing through their apps. Free JSDefender evaluations are available and can be purchased as part of a PreEmptive Protection subscription.

JetPatch 4.0
JetPatch 4.0 adds machine learning and intelligent workflow automation capabilities to ensure that an organization’s systems are appropriately patched. The latest release minimizes the time it takes to remediate a vulnerability once it’s discovered, allowing JetPatch to substantially improve an organization’s security posture.
JetPatch said its predictive patching machine-learning technology diagnoses remediation cycles and provides actionable insight derived from the data to increase success. It also slashes time to remediation, JetPatch said, transitioning vulnerability efforts from fragmented manual processes into one orchestrated and governed operation.
All told, the company said JetPatch 4.0 allows business leaders to transform the way their organization combats vulnerabilities and shift to a single predicted, governed vulnerability remediation process.

White Ops Application Integrity
White Ops Application Integrity is designed to protect enterprises from sophisticated bot-based threats including account takeover, automated account creation, and web scraping. The offering protects enterprises against sophisticated bot attacks by leveraging White Ops’ scale and accuracy, real-time prevention and takedown capabilities, and multilayered detection methodology.
By incorporating technical evidence, machine learning, continuous adaptation of detection techniques and threat intelligence, this methodology enables Application Integrity to identify and block bot traffic with the highest degree of accuracy and speed to stay ahead of adversaries. Application Integrity can identify bots with the highest degree of confidence even in low signal environments, White Ops said.
The offering provides rationale behind each detected sophisticated bot, gaining better insight and context into the origin and tactics of the bot attacks on the applications. In addition, Application Integrity secures user accounts against unauthorized access and prevents fraudulent new accounts from being created.
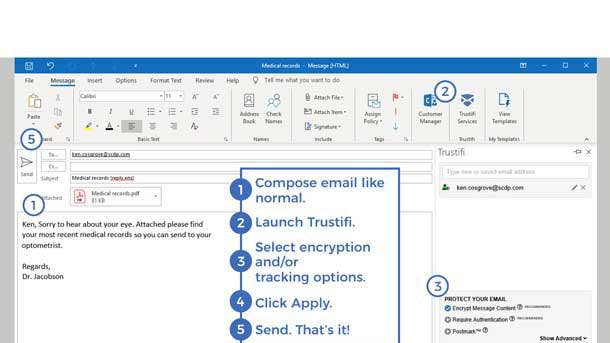
Trustifi Email Encryption
Trustifi has developed an offering that simplifies both the receipt and transmission of encrypted emails, making it just as easy to send a 256-bit AES encrypted message as it is to transmit any other email. Trustifi’s offering allows users to send encrypted emails simply by clicking a box in Microsoft Office or Gmail, which can speed adoption of secure environments.
In addition to offering email encryption, Trustifi accommodates security for both inbound and outbound emails on a single solution, simplifying security management for organizations and minimizing complicated procedures typically associated with encryption systems. Meanwhile, the data loss prevention and advanced threat protection offerings address threats like phishing, viruses and spyware.
Trustifi said its offerings are customizable, competitively priced for a variety of business environments, and compliant with the most rigorous of security regulations include HIPAA, GDPR, PII and CCPA.
Essence SigmaDots
Essence SigmaDots has developed a comprehensive cybersecurity tool that harnesses the power of distributed architecture to completely secure IoT devices, applications and data. The technology maximizes IoT security and minimizes the impact on the consumer by protecting the entire path, including device, network and system.
The SigmaDots platform is comprised of four pillars: on-the-edge dynamic firewall and antivirus; distributed MQTT networking protocol as a service; end-to-end encryption as a service; and cloud-agnostic/on-premises platform for cyber events, operational monitoring, and alerting. Essence said these pillars can be implemented independently or as a complete offering.
Taken together, the company said Essence SigmaDots enables complete network visibility, delivering insights into attacks and suspicious activities to the SOC, which in turn allows for a faster response.
42Crunch API Security Platform
A new registration feature on the 42Crunch API Security Platform gives development, security and operations teams instant access to a comprehensive set of API security tools that easily integrate into existing workflows and enable an agile DevSecOps process. The company said the new feature will make it easier for DevOps and Security teams to work seamlessly together to secure all their APIs in real time.
The new self-registration feature provides instant access to the security tools in the 42Crunch API Security Platform, allowing teams to deliver security across the entire API life cycle. The API Security Platform runs more than 200 audits of the OpenAPI specification definition with detailed security scoring to help developers define and strengthen API contracts.
The API Security Platform also scans live API endpoints to discover potential vulnerabilities and discrepancies of the API implementation against the API contract. From there, the platform launches a service to protect APIs and apply policies that can be deployed in the company’s lightweight, low-latency micro API firewall.

Chainkit by PencilData
Chainkit by PencilDATA creates irrefutable chains of custody for data, infrastructure and code using proven distributed ledger math. Establishing irrefutable data custody interrupts the attack chain the moment intruders attempt to establish command and control and/or tamper with data, giving users unprecedented early visibility into previously invisible break-ins.
Meanwhile, Chainkit for Splunk and Chainkit for ElasticSearch’s ELK Stack apply PencilData’s distributed ledger-based event log authentication against adversarial anti-forensics techniques. Integrations with Splunk and the ELK Stack enable customers to detect unauthorizing tampering with event logs and other anti-forensics techniques intruders use to hide evidence of their presence inside a network.
Chainkit is used by everyone from managed service providers and midsize enterprise customers to government agencies, Global 2000 and Fortune 500 companies to increase attack visibility, reduce threat dwell times, and proactively automate forensics-class audits to continuously thwart hacks.