Intel Tiger Lake CPUs Will Have Hardware-Based Malware Protection
The semiconductor giant plans to debut a new hardware-based security feature, called Intel Control-Flow Enforcement Technology, in future processors, starting with the Tiger Lake laptop chips, to protect against a class of malware that has typically been difficult to mitigate with software.
Intel plans to introduce new hardware-based protection against common malware attacks in the chipmaker's upcoming 10-nanometer Tiger Lake processors for laptops.
The Santa Clara, Calif.-based company announced on Monday that Tiger Lake, which will be sold in laptops under the Intel Core brand, would be the first family of processors to use the new Intel Control-Flow Enforcement Technology. Future server and desktop processors will also get the feature as will future vPro processors as part of the company's remote IT management platform.
[Related: Intel To Expand SGX Support For Xeon, Extend Hardware Security Capabilities]
It will be enabled through a feature in Windows 10 called Stack Protection, which Intel said is now available in Microsoft's latest preview build as part of the Windows Insider Program. Intel said it is also working with compiler vendors and software developers to support Intel Control-Flow Enforcement Technology, or CET for short.
More than 50 laptop designs coming out this holiday season are expected to use Intel's Tiger Lake processors, the successor to last year's Ice Lake, Intel CEO Bob Swan said in April.
Tom Garrison, vice president of Intel's Client Computing Group and general manager of Security Strategies and Initiatives, told CRN that Intel Control-Flow Enforcement Technology, or CET, is a set of silicon-level instructions that targets a malware type known as control-flow hijacking that has been traditionally difficult to mitigate through software, which is what prompted Intel to develop the feature.
"It was something that needed a company like Intel to stand up and deliver a hardware-based solution, but also to do it at scale with our partners and deliver it throughout the ecosystem," he said.
Control-flow hijacking attacks are a prevalent type of malware, according to Garrison, that involves manipulating memory and using jump- or call-oriented programming or return-oriented programming to modify existing code. Because it involves modifying existing code of an application, like a web browser, to carry out malicious actions, traditional anti-virus software can't detect it, he said.
"They manipulate the code in ways that were never intended to get whatever result they're looking for," Garrison said."
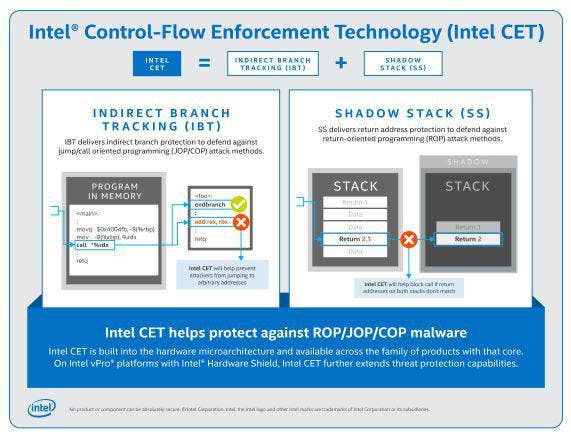
To protect against these types of attacks, Intel CET has two key capabilities. The first one, indirect branch tracking, protects against jump-oriented programming by preventing attackers from jumping to an arbitrary part of the code and instead forcing them to the end branch of an address, ensuring that the attacker can't modify the code in an unintended way.
The second, shadow stack, is enabled at the operating system level and acts as a mirror copy of the return addresses of an application. If a return address is modified and doesn't match its mirror copy in the shadow stack, CET will prevent the code from being executed and will return an error.
"The idea there is that if they don't match it, it's because somebody manipulated the address, and it flags that as an error, and it's detected," Garrison said.
Garrison said the performance impact of CET is "very minimal."
While shadow stack is a capability that needs to be supported at the operating system level, indirect branch tracking will be enabled for developers at the compiler level, according to Garrison.
"The compiler that they use will be enabled with CET. That's where most of the work is," he said.
Kent Tibbils, vice president of marketing at ASI, a Fremont, Calif.-based Intel distributor, said the new CET feature will help give Intel a competitive edge, particularly with commercial organizations that are making endpoint security a higher priority as many employees continue to work from home.
"Security was on peoples' mind to begin with prior to everything happening" with the coronavirus pandemic, he said, "but I think it's gaining even more and more momentum and becoming a higher and higher priority for people to think about, not just protecting their data but all these other elements and ways they might be vulnerable to an attack."
With the new security capabilities, solution providers can use them as a starting point for a bigger conversation about security with customers, according to Tibbils.
"The end clients are more aware of it, they're more open to those discussions, and these things can lead to other value-add opportunities that the reseller can bring into what they're offering," he said. "It's not just, hey the processor has these new hardware capabilities built into it that are going to help protect you.' It helps expand that conversation into other areas where they can have further discussions about how customers are securing and managing their remote workforce."