Google Cloud Unveils New BeyondCorp Zero Trust Security Platform
‘Google has built a reputation and a pedigree of sharing and bringing to market the champagne that they drink in-house,’ says Arun Perinkolam, Deloitte Consulting’s Google Cloud cyber practice leader.
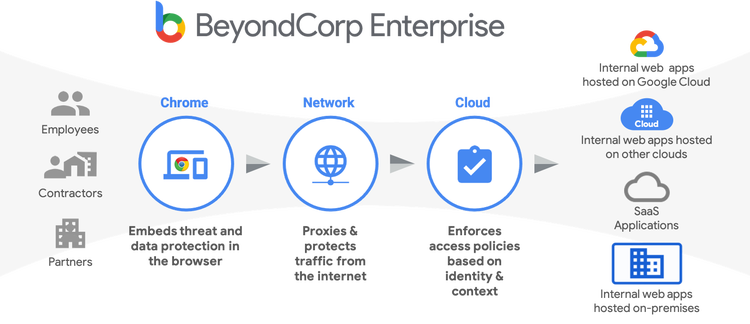
Google Cloud Tuesday unveiled BeyondCorp Enterprise, its new zero trust identity and security platform with agentless support delivered through Google’s Chrome browser that’s used by more than 2 billion users globally.
Now generally available, BeyondCorp Enterprise is designed to provide continuous and real-time end-to-end protection, scalable DDoS protection and built-in, verifiable platform security. It includes embedded data and threat protection built into Chrome—which has been quietly updated already— to prevent malicious or unintentional data loss and exfiltration and malware infections from the network to the browser; phishing-resistant authentication; and continuous authorization for all interactions between a user and BeyondCorp-protected resources.
Many of the zero trust options from other providers focus on the connection from the user to the app or the user to the network, according to Rick Caccia, Google Cloud security’s marketing head. BeyondCorp Enterprise is the only system where every single interaction—from user to app, app to app to other infrastructure components all the way through—is reauthorized, Caccia said.
“The years of security we’ve built into the system enables the trust that cloud users need,” Caccia said.
The turnkey product offering encompasses a series of functionalities that leverage what Sunil Potti, general manager and vice president of cloud security for Google Cloud, calls “significant amplifiers that only Google can provide.”
“Essentially, all of our PoPs [points of presence] now are lighted up with the same functionality that powers Google employees,” Potti said. “[They’re] now available to essentially both protect, but also transit, the Google network from wherever users are to wherever their apps are in the form of BeyondCorp Enterprise.”
The offering extends to connections to Google’s 144 global network edge locations.
The Chrome browser now has built-in capabilities that use Google’s Cloud Data Loss Prevention and Safe Browsing APIs, a Google service that lets client applications check URLs against Google’s constantly updated lists of unsafe web resources.
“We worked with Chrome to build all those into BeyondCorp Enterprise and turn it on,” Caccia said. “It also uses things like two-factor keys so that we can prevent against phishing and credential theft. In the network itself, we have cloud-based micro-segmentation, so that every piece of the network implements authorizations, sort of from component to component. And we have our own global certificate management system built in that customers can use to make sure that they’ve got updated certs anywhere that encryption has to happen.”
As evidenced by the SolarWinds breach, being able to verify a platform from chips to apps and having features such as binary authorization to make sure that apps haven’t had their source code tampered with are important, Caccia noted.
“All of those are in the network,” he said. “It means that customers can trust this as a platform to run on.”
Google Cloud’s BeyondCorp Approach
Zero trust is a security concept based on the premise that there is no inherent trust in a network, and that all access to a network must be secured, authorized and granted based on knowledge of identities and devices.
BeyondCorp refers to the zero trust access approach that Google Cloud started pursuing in 2011. It’s the technology suite that it uses internally to protect Google’s applications, data and users, allowing its own employees to work from untrusted networks on a variety of devices without using a client-side VPN.
“Given the new work-from-home environment, but also the recent attacks, ultimately someone has to come in and say, ‘Look, unlike a mobile world, where a new OS really had built-in security, we still live in a world of heterogenous OSes, whether it be public clouds, private clouds and so forth,” Potti said. “So unless we make a seismic change in terms of offering a zero trust OS of some sort as a layer that sits on top of this hybrid environment, I don’t think we’ll ever make a sea change in terms of trust and risk management. That’s really the genesis behind how we’re thinking about BeyondCorp Enterprise as a truly comprehensive view towards zero trust.”
BeyondCorp Enterprise extends and replaces BeyondCorp Remote Access, Google’s cloud offering introduced last April that allows organizations’ employees and extended workforces to access internal web applications—customer service systems, call center applications, software bug trackers, project management dashboards, employee portals—from almost any device, without a traditional remote-access VPN, while protecting their data.
“Post-COVID, we were able to give what I call a ‘downpayment’ on the uber zero trust offering that we’ve been working on for a few years in terms of packaging BeyondCorp in its entirety, not just in a piecemeal solution, so that customers anywhere could consume the same capabilities that we currently use to protect our employees and our applications and so forth,” Potti said.
The challenge in developing BeyondCorp Enterprise was enabling disruptive security innovation with a cost-effective offering that requires minimal disruption to existing deployments and business processes, according to Potti.
BeyondCorp Enterprise Partner Ecosystem
Google Cloud designed BeyondCorp Enterprise as an open and extensible offering that can support a variety of complementary security offerings from its BeyondCorp Alliance partners. It intentionally built a forward-looking ability to seamlessly plug in services and value-adds, both in terms of new capabilities on the endpoint or inside the network close to the app, and exchange data and signals, so the overall “IQ” of the system is improving with a partner ecosystem, according to Potti.
That ecosystem includes Citrix Systems, CrowdStrike, VMware and Tanium, a Kirkland, Wash.-based endpoint management and security provider, among others.
“For most devices, there’s more to them than the browser, and that’s where a partner like Tanium [comes in with] their ability to manage the endpoint, make sure there are patches and also to detect and block threats on there,” Caccia said. “Working together, we have APIs that the two products use so that we can understand the endpoint. Chrome browser drives that, and Tanium can drive that.”
Tanium’s customers include 70 Fortune 100 companies and the U.S. Department of Defense, which have been struggling with need to move toward zero trust.
“What the industry historically has presented to them was a very fractured model for this, so that, in essence, they had to cobble together potentially 10 different vendors to get a contiguous zero trust experience,” said Orion Hindawi, Tanium’s co-founder and CEO. “Just keeping that working was something that was beyond the vast majority of companies.”
Managing the endpoint state is required to implement zero trust, and Tanium had been waiting for a provider to come out with a fabric that would allow a contiguous solution, according to Hindawi.
“It’s incredibly convenient that it’s Google, because I think Google, if you look internally, is by far the leading implementer of zero trust in industry in production,” he said. “What we’ve been able to do with them has been really novel in the sense that we’ve been able to spend a lot of time customizing the interfaces that we’re supplying data into. Being able to change state and have that state reflect access and ability to use the environment in real time is incredibly critical.
“We’ve actually seen Google implement on the back end, at the kind of fabric layer, the ability to respond to those inputs incredibly quickly. If something isn’t patched correctly, or users are exhibiting behavior that you don’t expect, or potentially we see applications that are misbehaving, in real time, you need to be able to condition is identity granted, are you able to use applications,” Hindawi said.
From Tanium’s perspective, endpoint management is critical, according to Hindawi.
“Coupled with a really powerful zero trust element, we really think it can fundamentally transform the way that our customers perceive their responsibility for security,” he said. “And I think this is the first time actually in our industry where we’ve seen an end-to-end approach that looks like it’s absorbable by customers and that can actually give them the value that zero trust has been purported to provide for a long time, but that they’ve really been searching for a way to implement.”
Deloitte Consulting
Google Cloud will continue collaborating with Deloitte Consulting’s cyber practice to deliver end-to-end architecture, design and deployment services to customers.
“Google has built a reputation and a pedigree of sharing and bringing to market the champagne that they drink in-house,” said Arun Perinkolam, a Deloitte Consulting principal who serves as its Google Cloud cyber practice leader.
Organizations today are faced with the rapid dissolution of traditional network parameters as a result of the continued shift to the cloud and hybrid IT, according to Perinkolam.
“The challenges that organizations now have with traditional perimeter-centric security approaches and technologies have elevated the need for continuous verification of trust—across an organization’s device base, user base and application base,” Perinkolam said. “At Deloitte, we recognize the move to a zero trust model and mindset as the sustainable path forward for organizations who are looking to circumvent some of these challenges while creating a cybersecurity program that is truly next generation—one that can also help address the need for scale across hybrid IT environments and offer a simplified secure user experience. When we look at Google’s BeyondCorp technology offering, it’s able to address just that.”