10 Coolest Cloud Security Tools And Products 2022 (So Far)
From Google tested open-source software to recon intelligence tools, the cloud is generating plenty of security products these days.

The migration of so many companies to the cloud has created its own security challenges in recent years – and the cybersecurity industry is responding.
Every week, new cloud security tools and products are being unveiled by cybersecurity startups and established companies alike.
In some respects, the new offerings can roughly mimic on-premise security tools, but in other respects they’re entirely different in concept and substance.
CRN has looked at many cloud security products so far this year, offerings produced by and for big and small firms.
The following are just 10 of those cool products and tools.
* Google’s Open-Source Security Software
* Aqua Software Supply Chain Security
* Tufin Orchestration Suite R22-1
* CrowdStrike’s Humio for Falcon
* Google Confidential GKE Nodes
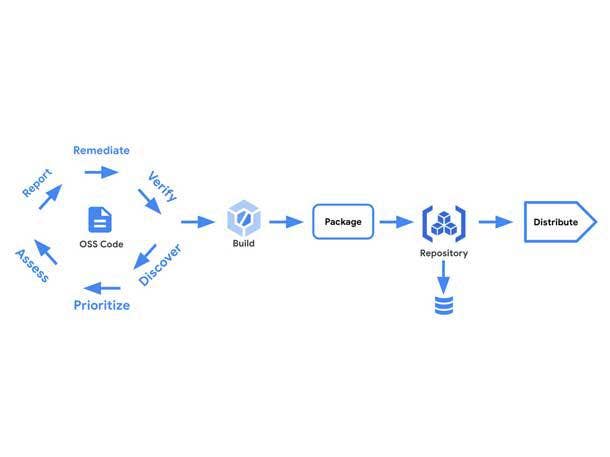
Google’s Open-Source Security Software
The vulnerability of software supply chains has become a major concern within the cybersecurity world. In May, Google Cloud took steps that could help deal with a portion of the supply-chain problem, announcing it was making available to customers some of its open-source security code that’s been previously tested and proven effective against cyberattacks.
The initiative, called Assured Open Source, is part of Google’s pledge last summer to spend $10 billion to improve cybersecurity across the Internet.

Aqua Software Supply Chain Security
Aqua Security, a cloud-native security company, is yet another firm focusing on supply chains, recently announcing that has integrated software supply chain security capabilities into its platform, following its acquisition last year of Argon Security.
“Aqua‘s cloud native application protection platform (CNAPP) is now the only solution on the market capable of securing the full software development lifecycle from code through build to runtime,” the company says.

Cisco Security Cloud
Cisco Systems made good use of last month’s RSA 2022 conference in San Francisco by unveiling its security vision moving forward to help enterprises connect their entire security architecture via a new platform called Cisco Security Cloud.
And there was a bonus announcement by Cisco, one that was highly anticipated: the launch of its second everything-as-a-service Cisco Plus offer for unified Secure Access Service Edge (SASE).

Chronicle Security
This past spring, Google Cloud subsidiary Chronicle Security made a series of announcements concerning security matters. Among others, it introduced new YARA-L functions for string matching, regex matching, timestamp operations and arithmetic operations in the Chronicle detection engine.
Chronicle Security also unveiled context-award detections to make alerts more functionally enabled and improve detection and response.
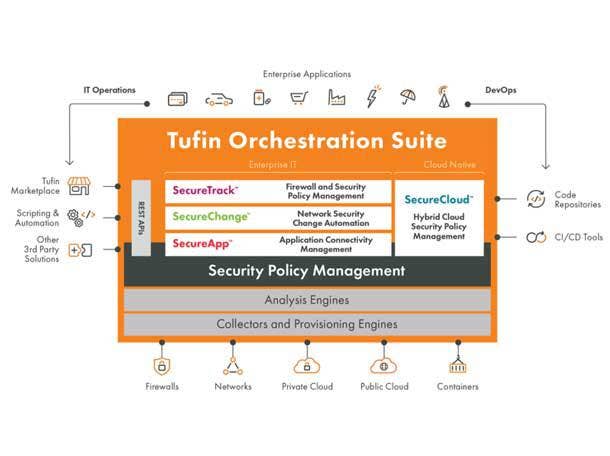
Tufin Orchestration Suite R22-1
Last month, Boston-based security policy management company Tufin announced it was expanding security policy automation capabilities for hybrid cloud environments, via its new Tufin Orchestration Suite R22-1. The company said the product enables users to increase their security posture by gaining visibility and control of Azure Firewall policies.
“Our latest release is a testament to our belief that a centralized, automated security policy solution can deliver security with agility in a hybrid multi-cloud world,” said Yoram Gronich, SVP of Products and Engineering, Tufin.

CrowdStrike’s Humio for Falcon
In June, Crowdstrike, a leader in cloud-delivered protection of endpoints, introduced ‘Humio for Falcon,’ which the company described as a “new capability that extends data retention of CrodStrike Falcon telemetry for “up to one year or longer, enhancing threat analytics and threat hunting abilities for organizations while helping them meet compliance requirements.”
The company timed the announcement to coincide with RSA 2022 in San Francisco.
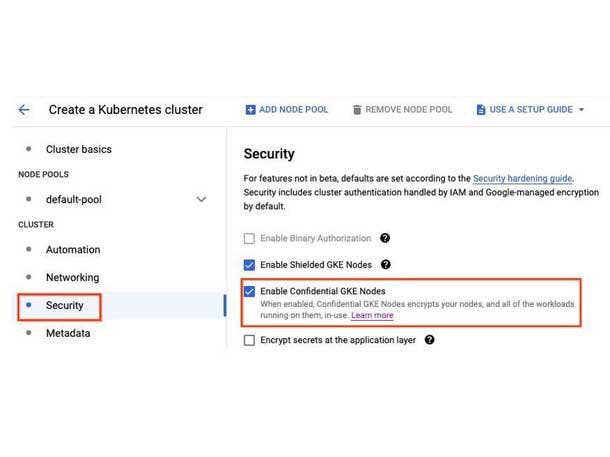
Google Confidential GKE Nodes
Earlier this year, Google launched the general availability of “Confidential GKE Nodes,” which the company says leverages hardware to make sure data is encrypted in memory. Confidential GKE Nodes are built on the same technology foundation as Confidential VM and utilize AMD Secure Encrypted Virtualization.
Orca Cloud Security
Here’s a product that’s trying to weave more security protections into the software-development process. Orca Security of Portland, Oregon, announced in May what it described as the “industry’s first cloud security solution to provide context-aware Shift Left Security for cloud infrastructure and applications.”
The bottom line, as the company described it: “Orca Security helps DevOps teams understand the potential impact of security issues on cloud application production environments, and fix those issues earlier in the software development lifecycle (SDLC).”

Laminar Cloud Data Security Platform
In February, Laminar, the Tel Aviv and New York-based public cloud data security provider, announced the release of Laminar Cloud Data Security Platform, which the company says is built on a “major architectural breakthrough” that enables data protection across the entire multi-cloud environment.
Laminar recently raised another $30 million in funding, with Tiger Global Management and Salesforce Venture were among the firm’s latest investors.
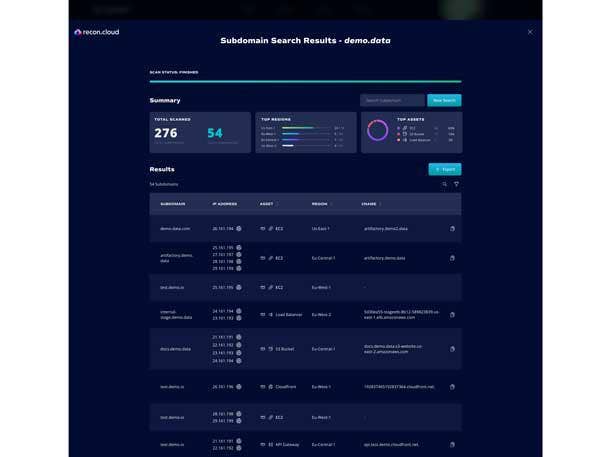
Lightspin’s Recon.Cloud
Let’s face it: The only thing cooler than a cool product is a free cool product.
In April, the Tel Aviv-based Lightspin launched a free AWS cloud security tool, called Recon.Cloud, described as a reconnaissance tool that scans AWS environments from an attacker’s perspective – and relays the information back to defenders.
“With Recon.Cloud, we are helping to solve the issue of poor visibility in cloud environments,” said Gafnit Amiga, director of Security Research at Lightspin. “Recon.Cloud is specifically designed to focus on only the pertinent publicly exposed cloud assets in a domain.”