10 Hot New Cloud Security Tools In 2023
As cloud security threats surge, a broad array of new tools from both industry giants and fast-growing startups have been released in recent months.

New Cloud Security Tools To Know
There’s no doubt about it: A growing number of threat actors are becoming “cloud-conscious,” as CrowdStrike researchers put it in their 2023 Global Threat Report. Such attackers are both well-aware that cloud workloads can be compromised and are actively exploiting cloud-specific features using this knowledge, the researchers wrote. As evidence of the growing cloud security threat, CrowdStrike reported that cloud exploitation cases surged by 95 percent last year, compared to 2021. For cybercriminal and nation-state threat actors alike, there’s a clear move toward “adopting knowledge and tradecraft to increasingly exploit cloud environments,” the researchers wrote in the report, including AWS, Microsoft Azure and Google Cloud.
[Related: 10 Emerging Cybersecurity Threats And Hacker Tactics In 2023]
As a result, cloud security is becoming a leading priority for a greater number of partners, customers and vendors in 2023. In terms of vendors, within the cybersecurity industry, a number of fast-growing startups have been focused on offering cloud security tools from the get-go. Venture-backed companies that’ve been doing cloud security since their inception include Wiz — the top-valued cybersecurity unicorn at $10 billion — and Orca Security, which sports a valuation of $1.8 billion. Meanwhile, numerous major security industry players have expanded into the category over time, including cybersecurity giants such as Palo Alto Networks and CrowdStrike.
As for the cloud security market overall, Gartner disclosed last week that it is expected to remain the fastest-growing area of security and risk management spending in both 2023 and 2024. Cloud security spending for 2023 is on track to climb 25.2 percent to $5.61 billion, year-over-year, before growing another 24.7 percent in 2024 to reach $7 billion, the research firm reported. Adding in application security — a category that increasingly overlaps with cloud security as apps continue shifting to the cloud — contributes an additional $5.77 billion in spending this year and a forecasted $6.67 billion in spending for 2024, according to Gartner.
All About CNAPP
Among the notable trends in cloud security is the fact that a large portion of vendors are now aligning to the Gartner-coined concept of a CNAPP, or cloud-native application protection platform, according to Mark Wah, vice president and analyst at Gartner. The CNAPP concept involves bringing together numerous key capabilities in security for cloud environments and cloud-native applications into a unified platform — improving cloud threat prioritization and making it easier for security teams to manage the tools. Core CNAPP capabilities include a variety of acronyms: Cloud security posture management (CSPM), cloud workload protection (CWP), cloud infrastructure entitlements management (CIEM) and more.
The fact that so many cybersecurity vendors are on the path of building out a complete CNAPP has been helping to drive many of the new cloud security and application security product launches this year. For instance, one major recent development in the CNAPP space is the realization by many customers that the “previous positioning of agentless approaches to CSPM may not be sufficient to cover runtime,” Wah said. That has contributed to influencing vendors such as Wiz, which initially only provided periodic snapshot scanning, to expand to offer capabilities for real-time detection of cloud workload threats.
That’s just one among the broad array of new cloud security tools that’ve been unveiled by key industry vendors in 2023 for protecting the use of public cloud environments such as AWS, Azure and GCP. As part of CRN’s Cybersecurity Week 2023, we’ve collected details on 10 recently introduced cloud security products that’ve hit our radar — ranging from industry giants such as Microsoft down to startups such as Ermetic, which saw its $265 million acquisition by Tenable reach completion Monday.
What follows are 10 hot new cloud security tools to know in 2023.

Aqua Security AI-Guided Remediation
Aqua Security added capabilities leveraging AI technologies—including generative AI—for improved remediation of cloud security issues. The new AI-Guided Remediation capabilities are available on the Aqua Cloud Security Platform to help security teams to “better operationalize risk findings to rapidly reduce risk and help developers quickly fix issues,” the company said in a news release. Using the tool, development and security teams can generate detailed remediation steps automatically and do so for “any misconfigurations and vulnerabilities across multiple clouds and workload types,” Aqua Security said.

Check Point Effective Risk Management
Check Point Software Technologies unveiled a new risk management engine, enabling improved cybersecurity risk prioritization on its CloudGuard CNAPP (cloud-native application protection platform). The Effective Risk Management offering combines with other tools on the CloudGuard platform to provide “smart risk prioritization that allows teams to quickly eliminate critical vulnerabilities, such as misconfigurations and over-privileged access, based on severity throughout the software development lifecycle,” Check Point said in a news release. The engine leverages “full context” for its risk prioritization, including workload posture, access permissions for identities and attack path analysis — as well as the business value of the application, according to the company.

CrowdStrike 1-Click XDR
For its Falcon Cloud Security offering, CrowdStrike introduced a number of notable updates including its new “1-Click XDR” capability. The tool works by automatically identifying unprotected cloud workloads and then deploying the company’s Falcon agent to secure them, CrowdStrike said. Other new Falcon Cloud Security capabilities added by CrowdStrike included agentless snapshot scanning for gaining visibility around cloud workload risk in situations where it’s not possible to install an agent; “complete” cloud attack path visualization, which provides a “unified view of the attack path, from host to cloud”; and an updated compliance dashboard that supports CIS, NIST, PCI and SOC2, as well as custom frameworks.

Ermetic Kubernetes Security Posture Management
Cloud identity and permissions management startup Ermetic, now owned by Tenable, announced an expansion of its CNAPP (cloud-native application protection platform) with the launch of Kubernetes Security Posture Management. The tool offers an automated way for the discovery — and remediation — of misconfigurations, privilege risks and compliance violations within Kubernetes clusters, according to Ermetic. To accomplish this, the tool utilizes signals from Ermetic’s other capabilities within its CNAPP to “provide full context visibility into threats,” the company said in a news release.

Lacework CIEM
Lacework debuted new capabilities aimed at allowing partners and customers to more easily pinpoint the cloud identities that pose a security risk, while also providing recommendations for how to mitigate the issues. The Lacework CIEM (cloud infrastructure entitlement management) capabilities utilize the company’s Polygraph machine learning engine, and involve dynamic discovery of cloud identities — across users, groups, roles and resources — to uncover cases of excessive privilege. Lacework’s technology then comes up with a risk score for every identity and discovers the highest-risk identities using attack path analysis functionality, according to the company. The platform ultimately is able to automatically generate recommendations for resetting permissions to the correct level, Lacework said.

Microsoft Defender CSPM
Microsoft announced general availability for Cloud Security Posture Management capabilities within its Defender for Cloud offering. The Microsoft Defender CSPM tool enables “end-to-end” visibility into security risks and prioritization of remediation efforts across an organization’s multi-cloud environment, the company said. Microsoft also said it has introduced “data-aware” security posture capabilities that enable automatic discovery of an organization’s data estate — as well as assessment of threats to sensitive data and prevention of breaches on likely attack paths.
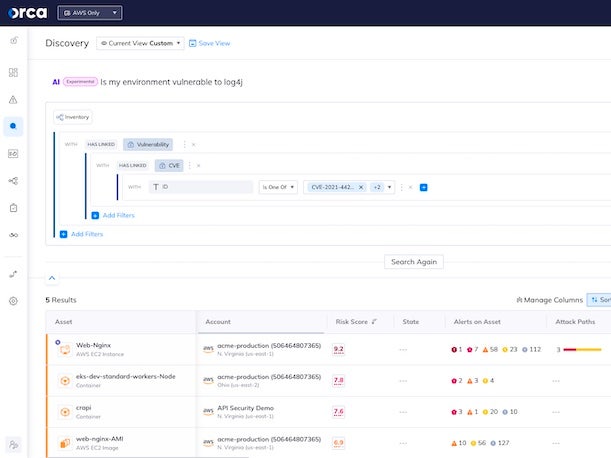
Orca Security AI-Driven Cloud Asset Search
For its Orca Cloud Security Platform, the company debuted AI-driven cloud asset search that utilizes Large Language Models (LLMs) to enable question-and-answer functionality around assets in the cloud. The generative AI tool makes Orca “the first cloud security provider to offer AI-powered cloud asset search that is as intuitive as asking a question,” the company said in a news release. And while the tool can be useful for security practitioners — for more quickly spotting cyber risks such as vulnerabilities in public-facing assets — the capability can also be used by developers, cloud architects and any others who are looking for a faster way to get visibility into their cloud environments, Orca said.

Palo Alto Networks CI/CD Security
Palo Alto Networks unveiled a CI/CD Security module to its Prisma Cloud CNAPP (cloud-native application protection platform). The new capability provides partners and customers with “integrated software delivery pipeline security,” the cybersecurity giant said in a news release.
One key benefit of the CI/CD Security module is that it offers unified visibility including code repositories and contributors, as well as any technologies and pipelines that are utilized, the company said in a blog post. The visibility is available through the newly added Application Security dashboard in Prisma Cloud.
Other benefits include enhanced protection against the 10 biggest CI/CD risks—as determined by the Open Worldwide Application Security Project—as well as posture management capabilities for delivery pipelines and attack path analysis, Palo Alto Networks said. Attack path analysis is available through the new Prisma Cloud Application Graph and enables improved understanding and analysis of the environment as well as “relationships between all artifacts from code to deployment,” the company said in the post.

SentinelOne Cloud Data Security
SentinelOne announced the debut of its new Cloud Data Security portfolio along with general availability for the initial two products that are part of it. The first of the new products — Threat Detection for Amazon S3 — is focused on protecting AWS customers that utilize Amazon S3 object storage. And with the second new product, Threat Detection for NetApp, SentinelOne is aiming to secure NetApp file storage for customers. In both products, the focus is around detection and prevention of malware within cloud environments, the company said. The products “automatically scan every file added to NetApp and object to Amazon S3 storage for file-born and zero-day malware,” SentinelOne said in a news release. And when the system detects a malicious file, SentinelOne automatically fixes the issue and quarantines the file, according to the company.
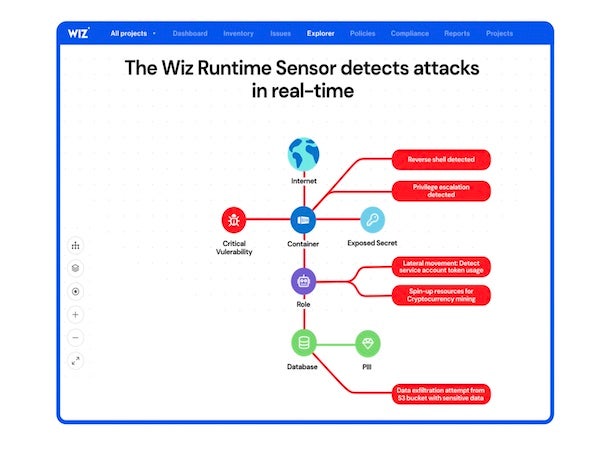
Wiz Runtime Sensor
After finding massive interest in its snapshot approach to rapidly gaining cloud security visibility, Wiz has added the ability to pinpoint threats that are impacting cloud workloads in real time with the introduction of its Runtime Sensor. The cloud threat detection and response offering works in tandem with the Wiz Security Graph to provide attack path analysis, which correlates real-time workload activities with cloud activities in order to spot suspicious behavior, Wiz said. Ultimately, by combining agentless snapshot scans of cloud environments with agent-based monitoring for cloud threats, Wiz can offer “full end-to-end visibility into attacks” — leading to a faster and more-efficient response, the company said in a news release.
The company’s Runtime Sensor stands out as a detection and response tool that is “born for cloud,” Wiz CTO Ami Luttwak wrote in a blog. For instance, Wiz’s approach to detection and response involves only using the Runtime Sensor when necessary to “collect true runtime signals such as runtime network use, processes, and memory use” — allowing the agent to remain lightweight, he wrote. “Most signals, including vulnerabilities, host configurations and more, are still collected from our agentless API-based scan.”
Additionally, the Wiz Runtime Sensor produces workload signals that are “well-integrated” with surrounding activity in cloud and Kubernetes environments, Luttwak wrote. And the tool is also “specifically designed to protect cloud-native, highly ephemeral workloads, which sets it apart from traditional solutions that are focused on server or endpoint host-centric protection,” he said. “When malicious activity occurs on short-lived containers or other ephemeral resources, the Wiz Runtime Sensor detects it and associates the detection and response to the specific workload (e.g., a Kubernetes Deployment), enabling accurate surface and scope for responding to the threat.”