ScanSource Ransomware Attack: 5 Big Things To Know
The attack, which has crippled some of ScanSource’s basic digital systems including parts of its website, comes as some cyberthreat experts report a resurgence in ransomware attacks in 2023 following the decline in attacks last year.

ScanSource Hit Hard By Ransomware Attack
Amid what some cyberthreat experts are saying is a resurgence in ransomware overall in 2023, IT and telecom distributor ScanSource confirmed this week it has become the victim of what appears to be a major ransomware attack. The cyberattack has crippled some of ScanSource’s basic digital systems, including many pages on its website, impacting customers and suppliers in geographies including North America, according to the Greenville, S.C.-based company.
[Related: 5 Things To Know On The Big Drop In Ransomware Attacks]
While total ransomware attacks fell in 2022 from the peak of the prior year, there has been a “substantial increase” on several barometers of ransomware activity in 2023 so far, said Mark Lance, vice president for DFIR and threat intelligence at GuidePoint Security, in an interview with CRN last week.
The ScanSource ransomware attack is also just the latest cybersecurity incident to strike a major player in the channel. Key ScanSource technology areas include security, networking, collaboration, connectivity and cloud services. The company reported earlier this month that net sales for the third quarter of its fiscal 2023, ended March 31, rose 4.7 percent year-over-year to reach $885 million.
In spite of the continued impacts from the ScanSource ransomware attack, shares in the publicly traded company rose Wednesday, with ScanSource’s stock price closing 1 percent higher at $28.67 a share. That gave the distributor a market capitalization of $713.88 million as of the end of regular trading Wednesday, according to Yahoo Finance.
What follows are five key things to know about the ScanSource ransomware attack.

The Timing Of The Attack
In a Tuesday news release, ScanSource said it “was subject to a ransomware attack that has impacted some of its systems.” The company said in the release that the incident had been discovered on Sunday.
The impacts to ScanSource systems appears to have been ongoing for days. BleepingComputer reported that ScanSource customers had been contacting the outlet, since Monday, to report that they were unable to access to ScanSource’s websites and customer portals.
After discovering the attack on Sunday, ScanSource said it “immediately” began investigating while also implementing the company’s incident response plan.
ScanSource is also the parent company of Intelisys and intY, but those websites appeared to be functioning normally as of Wednesday.
Impacts From The Attack
In its news release, ScanSource did not go into detail on which systems have been impacted, but referred to an “impact on its employees, customers and suppliers” and pointed to North America as among the affected geographies. “ScanSource regrets any inconvenience or delays in business this may cause customers and suppliers in North America and Brazil and appreciates their patience,” the company said in the release.
In an email to CRN Wednesday, ScanSource said it had no further details on which systems in particular have been impacted. It was not immediately known if the perpetrators of the attack had also stolen data from ScanSource, in addition to deploying ransomware.
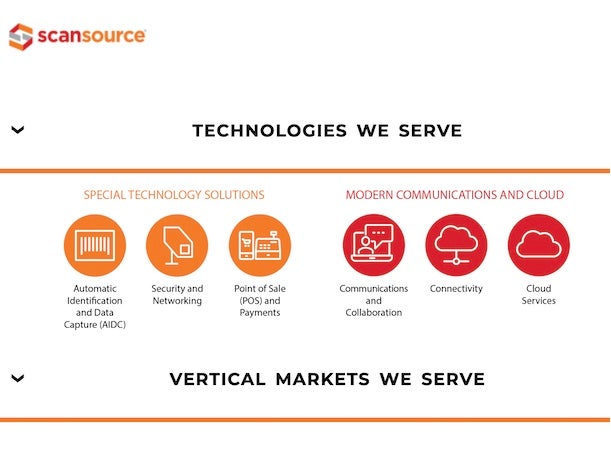
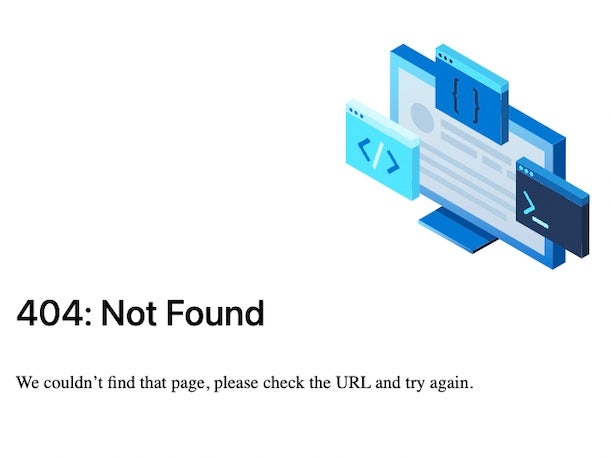
As of Wednesday, it appeared that scansource.com was still experiencing substantial impacts from the attack. While a homepage for the website was still viewable, it appeared to have been significantly scaled back in terms of its functionality (pictured above). While the homepage presented information about ScanSource’s offerings, links to other pages had been largely removed from the homepage. Meanwhile, a number of pages on scansource.com viewed by CRN Wednesday were displaying a “404: Not Found” message. Those included pages on ScanSource focus areas such as networking and security, the company’s “about us” page and the MyScanSource account portal page used by customers.
No ETA On System Restoration
In an email responding to questions from CRN Wednesday, ScanSource declined to say whether there is any estimate about the timetable for restoration of the systems. In its news release Tuesday, ScanSource had said it is “working quickly to get its business fully operational.”
The company said in the news release that it is “working closely with forensic and cybersecurity experts to investigate the extent of the incident, minimize disruption and mitigate the situation.” The company has also contacted law enforcement about the incident.
ScanSource added that it is “working diligently to bring affected systems back online, while also mitigating the impact on its business.”

Ransomware Resurgence?
Ransomware was actually down in 2022, according to research reports from several cybersecurity vendors. SonicWall, for instance, reported that global ransomware volume dropped by 21 percent in 2022, and by 48 percent in the U.S. At Mandiant, meanwhile, 18 percent of intrusions that its team investigated involved ransomware in 2022, down from 23 percent the previous year. The declines last year came after the record-shattering ransomware year of 2021, and at least some of the drop was thanks to improved prevention and law enforcement intervention, experts have told CRN.
However, the ScanSource attack may be just the latest sign that ransomware is regaining ground in 2023. Major attacks this year have included the widespread ESXiArgs ransomware campaign, which compromised thousands of VMware ESXi servers in Europe and North America in February by exploiting a two-year-old vulnerability.
On the whole, ransomware-focused threat actors “came out of the gates gunning” in 2023, said GuidePoint Security’s Lance. Ransomware activity during the first quarter of the year, for instance, was “back to rates that were more [in line with what] we saw in 2021,” he said in the interview with CRN last week.
“Specifically, we’ve seen a substantial increase in the amount of public [ransomware] victims that are posted,” Lance said. “And even us, working ransomware engagements and responding [to the attacks], we have definitely seen that come back to 2021-type volumes.”
Channel Players Targeted
ScanSource is far from the first major player in the channel to become the victim of a significant cyberattack, of course. The ScanSource ransomware attack serves as another reminder that even the businesses that making their living from technology products and services — including in cybersecurity — are in no way immune to the massive threat posed by cybercriminals.
In July 2022, IT solution provider powerhouse SHI International confirmed it was hit by a “coordinated and professional malware attack” over the Fourth of July holiday weekend. More than a week after the attack, SHI International said that the “vast majority” of its internal and external-facing systems were “fully operational.”
In late July 2021, Accenture suffered a cyberattack that utilized the LockBit ransomware. After containing the incident and isolating impacted servers, “we fully restored our affected servers from back up,” Accenture said in a statement in August 2021.
In 2020, major solution providers that were struck by ransomware incidents included Cognizant, Conduent, DXC Technology and Tyler Technologies.