The 2018 Tech Innovator Awards

Groundbreaking Innovation
As digital transformation only quickens its pace—and becomes nothing short of a necessity for many organizations—solution providers that can spot the next killer innovation are in greater demand than ever before. Solution providers that are able to demonstrate true differentiation have no shortage of opportunities in building new businesses or gaining additional business in existing ones.
Ultimately, what innovation does is give solution providers more opportunities to strike up a conversation with customers both old and new. And whether it’s in cloud, security, infrastructure or devices, the innovations you’ll find in this year's Tech Innovator Awards are true conversation starters.
The awards this year honor groundbreaking vendors in 35 categories, with the winners and finalists chosen by the CRN staff from among 296 applicants. The ability to help solution providers differentiate themselves and grow their businesses is the crowning achievement of all of our Tech Innovator winners and finalists, which appear on the following pages.
Business Intelligence and Analytics
Winner:
Cisco AppDynamics Business iQ
Cisco-owned AppDynamics has brought a number of powerful enhancements to the latest release of its Business iQ platform, with a focus on adding visibility into Internet of Things deployments and bringing together distributed business events for improved customer interactions. The addition of IoT visibility enables deeper insight into the way that devices are impacting the business, while also offering a simplified view into issues such as device uptime and performance for improved troubleshooting. Business iQ also links together different business events through its Business Journeys feature as a way to show organizations how their customers are truly interacting with them.
Finalists:
A10 Harmony Controller
With Harmony Controller, A10 Networks is offering an integrated solution for application delivery and security that provides collection, analysis and reporting on application traffic. The solution brings process and deployment automation as a way to boost productivity and effectiveness of personnel.
DataRobot Time Series
Leveraging advanced machine-learning technologies and time series methods such as Facebook Prophet, DataRobot’s Time Series solution offers a way to automate the development of models for time series forecasting, enabling the creation of highly accurate forecasts.
Kentik Hyperscale Custom Dimensions
Kentik’s Hyperscale Custom Dimensions offering targets major improvements for the value that can be gleaned from IT infrastructure telemetry data—ultimately translating data into actionable insight while also reducing manual effort. The offering also produces results in rapid fashion.
MapR Data Platform 6.1
MapR's Data Platform 6.1 release expands access to cloud and edge device data while also simplifying the development and deployment of AI and analytical applications. Key updates include the introduction of native API access to Amazon Web Services S3 storage.
Cloud Backup/Disaster Recovery
Winner:
Scale Computing HC3 Cloud Unity DRaaS
Cloud Unity combines Scale Computing’s HC3 on-premises appliance-based hyper-converged infrastructure with the Google Cloud Platform, allowing businesses to use resources in the cloud and on-premises simultaneously, as well as enabling on-premises applications to run in the cloud via virtual machine instances of HC3. The offering allows for seamless disaster recovery because the IP address of the workload looks the same in Google, eliminating the need for a VPN. Importantly, Scale Computing’s HC3 features built-in software-defined networking to simplify the disaster recovery setup. Cloud Unity ultimately provides partners with an easy way to implement cloud-based disaster recovery solutions with predictable costs.
Finalists:
Cohesity CloudSpin
CloudSpin, which offers instant access to data copies in the cloud, pairs with native API integration in Cohesity’s DataPlatform to provide web-scale backup to organizations. The solution provides automated data protection by integrating with public cloud snapshot APIs.
Commvault HyperScale
With an eye toward hybrid environments, Commvault’s HyperScale software adds scale-out infrastructure to the Commvault Data Platform—integrating seamlessly with existing storage arrays, hypervisors, applications and cloud provider solutions. The system includes a built-in operating environment, virtualization and Red Hat storage.
Dell EMC IDPA DP4400
Dell EMC’s DP4400 appliance offers converged data protection, backup, deduplication, replication and recovery, as well as disaster recovery and long-term data retention to the cloud. Optimized for VMware environments, the integrated appliance enables administrators to perform backup and recovery tasks directly from native vSphere.
StorageCraft ShadowXafe
With ShadowXafe, StorageCraft is targeting virtualized servers with service-level-agreement-based data protection and simple, one-click orchestration. The software also provides flexible recovery of data protected with StorageCraft ShadowProtect, and works with both physical and virtual machines.
Cloud Platforms
Winner:
Nutanix Beam
The first-ever Software-as-a-Service offering from Nutanix, Beam enables customers to truly understand the costs around public cloud. Nutanix Beam offers multi-cloud governance so that customers can manage their spending, security and regulatory compliance across Amazon Web Services and Microsoft Azure. Crucially, Beam provides in-depth analysis of exactly how organizations are consuming public cloud services—showing what cloud services are being used, who’s using them, how much of those services are being consumed and how much it costs. Nutanix Beam ultimately enables partners to better manage and secure customers’ costs associated with public cloud workloads and applications.
Finalists:
Anaplan Workflow
A component of Anaplan’s Software-as-a-Service platform for “connected planning” at businesses, Anaplan Workflow provides capabilities such as Process Builder for defining steps in a plan; linking those steps to individuals or groups for taking certain actions; and then setting parameters for guiding participants through the execution of the plan.
Dropbox Business
A workspace hub for keeping teams organized and productive, Dropbox Business provides a centralized content location along with highly scalable administration and security features. Key capabilities include Smart Sync, which lets users access cloud-stored files from their desktop.
Virtustream Healthcare Cloud
Virtustream has updated its Healthcare Cloud—a cloud platform for supporting mission-critical health-care applications—to include disaster recovery and the availability of SAP Health, offering enhanced patient and operational insight to customers.
Zenoss Cloud
Powered by advances in data streaming and machine learning, the Zenoss Cloud platform offers intelligent IT operations management to provide context to organizations that are looking to prevent service disruptions. The platform differentiates with its capabilities for streaming and normalizing machine data.
Collaboration/Unified Communications Applications
Winner:
Intermedia Unite
Intermedia Unite combines Intermedia’s cloud-based voice solutions with AnyMeeting video conferencing technology to create an offering designed especially with the needs of small- and midsize-business customers in mind. The cloud-based unified communications offering provides voice, video, screen- and file-sharing and secure backup on an integrated platform that’s easy to install and manage for solution providers serving small-business customers. As many SMB customers are looking for collaboration tools, the Intermedia Unite platform with integrated videoconferencing and screen sharing allows solution providers to stay on the cutting edge by offering innovative features and functionality.
Finalists:
BlueJeans Rooms with Dolby Voice
For a cloud-based collaboration solution with superior video, audio and screen sharing, BlueJeans Rooms with Dolby Voice combines the Dolby Conference Phone, Dolby Voice Camera and Dolby Voice Hub with advanced capabilities in BlueJeans Rooms such as enterprise-caliber management and “one-touch” joining of meetings.
Broadvoice b-hive
With b-hive, Broadvoice is targeting SMBs by bundling UC-as-a-Service, collaboration and cloud-based contact center tools with the company’s redundant network and hosting infrastructure. The platform makes it easy to make changes or program voice systems directly from its web-based portal.
Cisco Webex Meetings
Cisco’s Webex Meetings provides a modern approach to video meetings with simplified scheduling and joining, with one-button to push for joining a meeting from any device (such mobile, browser and video room devices, including third-party devices). The solution integrates video with voice and content sharing for a full collaboration suite.
RingCentral Pulse
RingCentral Pulse provides offerings for improving customer service with monitoring of service and sales performance metrics, along with alerts that are sent directly to affected teams. The offering leverages intelligent bots for monitoring key call center metrics and sending out automated notifications and alerts.
Contact Center Applications
Winner:
Cisco Customer Journey Platform
Cisco’s Customer Journey Platform stands out in the market for providing superior contact center solutions with its use of data in multiple contact center systems and application of predictive analytics. The platform provides dynamic predictions of customer needs, enabling organizations to match each customer with the ideal agent. Aimed at the midmarket segment, the Customer Journey Platform is targeted at customers creating their first contact center, or who are seeking to improve contact center operations. Distributed contact centers can also benefit from leveraging the platform for improving visibility and contact over their sites.
Finalists:
CoreDial CoreNexa Contact Center
Mainly aimed at small and midsize businesses, CoreDial’s CoreNexa Contact Center offering is available as a private-label option that partners can provide under their own branding. Key features include self-service IVR, configurable automatic call distributor routing and real-time reporting.
Talkdesk Enterprise Contact Center Platform—CX Manager
Talkdesk’s CX Manager feature in its Enterprise Contact Center Platform offers a highly intuitive routing engine, which enables visual designs of customer journeys without the need for expensive IT resources or coding. With CX Manager, users can leverage a library of components for dropping into critical contact center actions.

Container Technology
Winner:
Pivotal Container Service
With the Pivotal Container Service, Pivotal has teamed up with VMware and Google Cloud Platform to offer open-source Kubernetes containers as a service and at large scale. The Pivotal Container Service brings enterprises and service providers a production-ready version of Kubernetes on VMware vSphere and Google Cloud Platform, with constant compatibility with Google’s container engine. The service also features cross-cloud security and network connectivity—including container network interface-compatible services powered by VMware NSX—and it is seamlessly integrated with VMware vSphere as part of VMware’s software-defined data center infrastructure for containers and virtual machines.
Finalists:
Aqua Container Security Platform
Aqua’s Container Security Platform integrates security directly into the DevOps pipeline, helping enforce policies and simplify compliance with regulatory requirements. The platform enables on-demand vulnerability scans for deployments built on the Amazon Web Services ECS container registry or on-premises.
Cisco Container Platform
The Cisco Container Platform offers a turnkey system designed to allow for deployment and management of containerized applications across public and private clouds—giving partners a clear path into lucrative application life-cycle management and other services sold on a recurring revenue basis.
IBM Spectrum Connect
With IBM Spectrum Connect, IBM block storage can be provisioned, monitored, automated and orchestrated in containerized environments (Docker and Kubernetes), as well as in VMware and Microsoft PowerShell environments. The solution ultimately offers greater simplicity and consistency across environments.
Rancher Labs—Rancher 2.0
Rancher 2.0 enables management of clusters orchestrated by different Kubernetes distributions across on-premises and cloud environments but scraps native support for other orchestrators. Previous versions of Rancher, an open-source management technology, only supported Rancher’s Kubernetes distribution.

Data Center Infrastructure
Winner:
HPE SimpliVity 2600
With its SimpliVity 2600 offering, Hewlett Packard Enterprise has introduced a breakthrough new way to extend its data virtualization solutions all the way to the edge. SimpliVity 2600 is a virtual desktop infrastructure (VDI) solution that brings together powerful data services for virtualized workloads with IT infrastructure. The solution creates a foundation for enhanced delivery of server, storage and networking services, and brings IT simplification through improved management, efficiency and protection of virtualized workloads. Targeted especially at deployments with limits on space, the SimpliVity 2600 hyper-converged solution provides strong partner opportunities for building a high-margin services business in the data center.
Finalists:
Apstra Operating System 2.2
Version 2.2 of Apstra’s Operating System (AOS) aims to help partners with moving legacy customer data centers into modern architectures, with its ability to automate multitenant Ethernet VPN across multiple vendors—the first such solution to offer such capabilities.
DriveScale Software Composable Infrastructure For Flash
With recent updates to DriveScale’s Software Composable Infrastructure—which connects high-performance storage to servers via Ethernet networking, and allocates capacity as needed—the company has added flash storage technology to target cloud-native applications including big data and NoSQL databases.
IBM VersaStack for IBM Cloud Private
The integration of VersaStack—a converged infrastructure offering combining IBM storage with Cisco compute and network elements—into the IBM Cloud Private application platform brings together public cloud simplicity with the benefits of on-premises implementations, such as security and performance.
Pure Storage AIRI
AIRI (Artificial Intelligence Ready Infrastructure) combines Pure Storage’s FlashBlade all-flash storage array for unstructured data, the Nvidia DGX-1 GPU-based platform for AI, and Pure Storage software for scaling systems to up to four nodes. AIRI is targeted specifically at ensuring data scientists have the data they need to be productive.
Data Management
Winner:
Veeam Availability Suite 9.5
For organizations that are seeking an autonomous model for data management, Veeam’s Availability Suite 9.5 ensures data availability regardless of where it’s residing, along with keeping IT apprised of where data is located and ensuring that data management meets compliance requirements. Meanwhile, Veeam’s new Availability Orchestrator capability provides improved orchestration of disaster recovery strategy through features such as automated documentation and testing, and offers easy reporting on crucial metrics. Veeam’s solutions ultimately help to evolve data management to behavior-based practices, rather than relying on policies.
Finalists:
Couchbase Data Platform 5.5
Aimed at aiding in the shift from legacy IT investments, Couchbase’s Data Platform 5.5 provides simplified management of applications along with greater agility in operations. That’s thanks to new additions such as the extension of SQL to support JSON data natively via N1QL queries.
IBM Spectrum Virtualize For Public Cloud
Bridging the gap between storage infrastructures and the public cloud, IBM Spectrum Virtualize for Public Cloud offers consistent storage management along with disaster recovery and application migration—as well as optimization for underlying IBM Public Cloud storage through capabilities including automated data placement.
Nutanix Era
Nutanix Era provides automated database provisioning and life-cycle management, extending the company’s Enterprise Cloud OS software stack beyond core Infrastructure-as-a-Service capabilities for private cloud environments to platform-layer services. Nutanix Era ultimately promises to bring one-click simplicity to database operations.
Rubrik Polaris Radar
Targeted at enabling faster recovery from security incidents, Rubrik’s Polaris Radar application brings together detection (aided by machine learning) with detailed analysis of impacts and a simplified approach to restores—all in a highly intuitive user interface.
Display LCD/Signage/Projection/GPU
Winner:
Samsung Flip
Samsung has charged into the booming market for large-format interactive conferencing displays with the debut of the Samsung Flip. The Flip is a 55-inch digital whiteboard aimed at improved workplace collaboration. One key differentiator is the ability to use the Samsung Flip either in the typical landscape mode or flipped to stand up in portrait mode. The display can be used as a digital flipchart for colleagues to use for drawing and writing notes, either with a digital pen or their finger. The Samsung Flip also comes with screen-sharing capabilities so that team members can remotely take part in meetings where the Flip is in use.
Finalists:
Aten Technology VE8950—4K HDMI over IP Extender
For delivery of 1080p/4K AV signals over long distances, Aten Technology’s VE8950 4K HDMI over IP Extender allows for low latency and is equipped to handle large-scale signal transmission and multiple displays. The offering also provides easy setup and operation and is ideal for environments such as trade shows and university campuses.
Epson LightScene Laser Projector
A new type of accent lighting laser projector, Epson’s LightScene can simultaneously project and illuminate immersive content—such as digital art and signage—on a wide range of surfaces and materials. Key applications for commercial signage with the LightScene projector include retail, hospitality and showrooms.
Sharp Electronics PN-V701 LCD Display
Sharp’s PN-V701 LCD Display offers a seamless, natural video experience thanks to its minimal 4.4mm bezel. Meanwhile, integrators constructing a video wall won’t need to assemble as many monitors with the 70-inch class monitor and small bezels, and the display can be set up either in portrait or landscape orientation.
Internet of Things
Winner:
Schneider Electric EcoStruxure IT Expert
Along with aiding in management of the data center, Schneider Electric’s EcoStruxure IT Expert cloud-based monitoring solution allows for management of edge computing systems thanks to its IoT-enabled architecture. The solution provides partners with real-time insight about devices, as well as visibility into the historic performance of the devices. Key capabilities include live data for 24/7 visibility, data-driven insight into the health status of connected devices and smart alarming—all of which can be delivered to a smartphone or tablet. Schneider Electric EcoStruxure IT Expert translates data, including from edge and IoT systems, into recommendations for taking proactive IT management actions.
Finalists:
Kisi Physical Security Platform
Kisi’s Physical Security Platform integrates physical security systems into IT infrastructure as a way to modernize the way buildings and workspaces are secured. The offering is connected across the hardware, database, credential and management levels, and provides simplified remote deployment of operations.
Ruckus IoT Suite
For organizations looking to build a secure IoT access network, the Ruckus IoT Suite combines distinct physical IoT networks together into a unified network—and brings the added benefit of slashing deployment costs by leveraging existing infrastructure for WLAN and LAN.
Senet Low Power Wide Area Virtual Network
With its Low Power Wide Area Virtual Network, Senet is offering a new approach to the delivery of IoT connectivity through a cloud-based architecture that's purpose-built for low-power WAN—ultimately modernizing IoT network deployment and device connectivity.
IT Automation Software
Winner:
Turbonomic 6.1
With recent updates to its platform, Turbonomic has been kicking its IT automation capabilities into high gear. Turbonomic stands out as a management tool with its ability to automatically take actions to optimize IT infrastructure and cloud environments for customers, ensuring that applications are supported with precise resourcing across hybrid deployments. Leveraging advances in artificial intelligence, Turbonomic 6.1 is able to guarantee application performance by making accurate resource placement decisions prior to workloads being built and after workloads are deployed. Ultimately, Turbonomic makes effective, automated decisions on workload placement and sizing all across an organization’s hybrid cloud deployment.
Finalists:
Cisco DNA Center Open Platform
By transforming its DNA Center intent-based networking control and management dashboard into an open platform, Cisco has enabled the automated management of any third-party device, including competing networking gear. The move has also created new opportunities for channel partners to develop applications for customers.
OpsRamp
OpsRamp stands out in the realm of IT operations management with a platform that is geared toward hybrid environments. The platform brings together discovery, monitoring,
Artificial Intelligence for IT Operations (AIOps) and event management in a single cloud-based offering, enabling IT infrastructure teams to act as service providers.
Puppet Enterprise 2017.3
Updates in Puppet Enterprise 2017.3 include the introduction of Puppet Tasks, which offers a simplified way to get started with automating tasks related to infrastructure and applications, as well as better coordination of new releases of the core Puppet components.
Rackspace Managed Services For Pivotal Cloud Foundry
For customers focused on application development using the Pivotal Cloud Foundry platform, Rackspace is providing management of the platform on any cloud—public or private—as well as in on-premises environments, helping to enable faster delivery of new applications.

Mobile Devices
Winner:
Samsung Galaxy Tab Active2
The Galaxy Tab Active2—a rugged 8-inch Android tablet aimed at verticals including manufacturing, transportation and retail—is the first LTE-enabled tablet from Samsung to be sold exclusively by the channel. The Tab Active2 is water- and dust-resistant and meets military ruggedness standards for drops, vibration, extreme temperatures and other impacts. Key features include the ability to use the tablet with many types of gloves, as well as a water-resistant S Pen that can be used even in the rain. The Tab Active2 also offers high brightness on the display of 480 nits, along with a removable battery for extending the tablet’s battery life.
Finalists:
Panasonic Toughbook FZ-T1
Bringing together military-standard durability and strong performance, the Panasonic Toughbook FZ-T1 is a 5-inch Android handheld for unpredictable work environments. The device is powered by a quad-core processor and offers features including an integrated bar-code reader, optional pistol grip with trigger and a warm-swappable battery for extended usage.
Zebra MC3300 Mobile Computer
Along with offering ruggedness features, warm-swap batteries, push-to-talk capabilities and data capture from as far as 70 feet, the Zebra MC3300 mobile computer stands out in its flexibility with four ways to configure—pistol-grip, turret with rotating head, straight shooter (0-degree scan) and 45-degree scan.

MSP Technology
Winner:
Pax8 Stax
Stax, a platform from cloud distributor Pax8, is a business intelligence dashboard for MSPs aimed at driving more cross-sell and upsell opportunities. Pax8 Stax stands out by giving MSPs the ability to visualize what cloud software offerings can be stacked together, taking into account data from other MSPs. The tool makes it easier for MSPs to offer a complete cloud solution stack to customers, with capabilities to instantly move a stack of products to new customers or users. The Pax8 Stax dashboard also provides increased visibility into cloud consumption trends that can pay off in higher profits for MSPs and cost savings for customers.
Finalists:
BitTitan MSPComplete
BitTitan’s MSPComplete, an IT services automation platform for managed service providers, offers an array of automated processes for key tasks in its Task Library, such as password resets, on-boarding/off-boarding employees and provisioning new Office 365 users—helping MSPs to scale their businesses while delivering top-notch customer experiences.
Continuum Managed Services Detect And Respond Endpoint
Continuum’s Managed Services Detect And Respond Endpoint is intended to help MSPs enhance their security toolkit through providing solutions for identifying and halting endpoint attacks, along with remediation services. The offering leverages Continuum’s around-the-clock security operations center for analysis, monitoring and threat intelligence.
Kaseya VSA
Recent enhancements to VSA, Kaseya’s remote monitoring and management software, include the ability for management of all IT assets from a centralized hub. The latest version also enables automation of routine IT tasks to cut back on support costs and features improvements to service levels and simplified management of remote and distributed environments.
Pulseway
With its mobile-optimized remote monitoring and management software—which is accessible to IT administrators from mobile devices—Pulseway provides critical capabilities such as OS patch management, advanced task automation, application monitoring, remote desktop, discovery and deployment.
Networking—Enterprise
Winner:
HPE Aruba Software-Defined Branch
With Software-Defined Branch, HPE Aruba introduces software-defined wide-area networking for branch locations with a powerful set of capabilities. The solution combines branch gateways and headend gateways with existing HPE Aruba technology—including ClearPass policy management software—to form an integrated SD-WAN, WLAN, LAN and security solution. The close integration allows HPE Aruba to simplify rules enforcement within the branch and provide a clear focus on data that either stays in the branch, is sent to a data center, or sent to the cloud. SD-Branch offers context, affordability and flexibility that make the system a major opportunity for partners.
Finalists:
Cisco SD-WAN for ISR
Powered by Cisco’s acquisition of Viptela, Cisco SD-WAN for ISR enables a secure end-to-end platform with a unified architecture connecting access, WAN, data center and cloud infrastructures/applications. Key capabilities include centralized management and visibility, optimized connectivity and automated workflows for public cloud and Software-as-a-Service.
CloudGenix AppFabric
CloudGenix is aiming to disrupt the software-defined wide-area networking space with its “application-aware” SD-WAN offering, AppFabric. The offering provides critical insight into the status of underlying WAN and applications, enabling improved performance, security and compliance.
Juniper EX4300 Multigigabit
Aimed at branch location and campus deployments, Juniper Networks' EX4300 Multigigabit Ethernet switch provides advantages including centralized management in the cloud, advanced security and hot-swappable components such as fans and power supplies—along with strong performance and availability.
Versa Networks Secure Cloud IP Platform
Among Versa Networks’ latest additions to its Versa Cloud IP platform include enabling the real-time assessment of voice and video sessions based on the quality and behavior of actual SD-WAN circuits, through Mean Opinion Score-based traffic engineering and reporting for unified communications services.

Networking—Voice/Video/Data
Winner:
8x8 X Series
With the X Series, 8x8 has brought together voice, video, collaboration and contact center into a single cloud platform. Like other 8x8 offerings, the X Series differentiates itself in part by providing entirely homegrown technology from 8x8 rather than using third-party providers for any of its components. Key capabilities of the X Series include advanced analytics around employee-customer interactions, enabling more-intelligent customer engagement for businesses. The X Series platform is available in multiple plan configurations with features including team messaging, unlimited global calling zones, increases in meeting participants and additional data analytics options.
Finalists:
Avaya CU-360 Collaboration Unit
Avaya’s CU-360 Collaboration Unit is an “all-in-one” offering for workplace videoconferencing featuring 4K or FHD video, a 4K camera sensor and a microphone array. The system connects to any third-party touch board as well as standard displays and offers easy setup with just two wires to connect.
LogMeIn Jive Voice
LogMeIn’s Jive Voice business phone system brings a born-in-the-cloud approach with voice functionality delivered through web, desktop and mobile apps; management of phone systems entirely through a web browser; and voice, video and chat capabilities available across device types.
Sennheiser SDW 5000 Business Headsets
Aimed at modern workspaces that are highly collaborative and mobile, Sennheiser’s SDW 5000 Business Headsets are able to easily connect to a range of devices—including desk phones, PCs, smartphones and other mobile devices. Key features include “super wideband” audio for superior sound and advanced security protocols.
Vonage Business Cloud
A cloud-native platform targeted at midmarket businesses, Vonage’s Business Cloud offers unified communications featuring tools for collaboration and conferencing, seamless integration with apps such as Office 365 and Salesforce, high reliability and a recently redesigned mobile app user interface.

Networking—Wireless
Winner:
Aerohive 802.11ax Access Points—600 Series
Aerohive Networks has been the first to market with access points on the high-performance 802.11ax standard with its 600 Series devices. The successor to 802.11ac, the 802.11ax standard—recently renamed Wi-Fi 6—is capable of dramatically improving Wi-Fi efficiency. Aerohive’s 802.11ax access points provide strong performance to a far higher density of users than access points using previous standards, thanks in part to new channel-sharing capabilities. The company’s AP650 and AP650X models feature software-defined dual 5GHz radios and 802.3bz backhaul connectivity, and the 600 Series offerings overall are particularly ideal for high-density environments such as university auditoriums and convention centers.
Finalists:
Ruckus E510
The Ruckus E510, an 802.11ac Wave 2 access point targeted at providing Wi-Fi to space-constrained and hard-to-reach areas, offers data rates of up to 867 Mbps and a design that allows it to blend aesthetically into outdoor deployment sites.
Cambium Networks PMP 450m
The PMP 450m, Cambium Networks’ massive 14 x 14 multi-user MIMO System, has received a number of recent updates including the addition of uplink multi-user MIMO for improved spectral efficiency and uplink throughput capabilities, as well as the launch of its technology in the 3GHz frequency band.
Mist Systems—Marvis Virtual Network Assistant
Mist’s AI-based Marvis virtual network assistant—which uses natural language processing to help troubleshoot Wi-Fi networks—brings a range of capabilities including answering hundreds of specific questions about network devices, as well as detection and reporting of anomalies.
Zyxel NebulaFlex
For business-class Zyxel access points, the NebulaFlex firmware upgrade brings the ability to manage access points either individually or as components of a broader network infrastructure that is cloud-managed. Using NebulaFlex requires no replacement of existing hardware and no additional hardware or software purchases.

PC Laptops
Winner:
HP EliteBook x360 1020 G2
Though it’s a notebook aimed at business users, HP’s EliteBook x360 1020 G2 features an ultra-sleek, compact design that is more reminiscent of consumer-focused laptops. The small size of the 12.5-inch notebook is especially impressive considering that it’s also a 2-in-1 convertible. The laptop is akin to carrying a paper notebook around, with a thickness just a bit over a half- inch and a weight of 2.5 pounds. But the EliteBook x360 1020 doesn’t compromise on performance with up to an Intel Core i7 processor, up to 16 GB of RAM and up to 15.5 hours of battery life—while its FHD display is seriously bright at 700 nits, too.
Finalist:
Acer Chromebook C732T
Targeted at verticals including education and health care, the Acer Chromebook C732T is a durable Chrome OS notebook featuring an 11.6-inch IPS touch screen that opens out to 180 degrees, military-standard drop protection, a spill-resistant keyboard and battery life of up to 12 hours on a charge.

PC Desktops/Monitors/Docks
Winner:
HP EliteOne 1000 AiO
With the EliteOne 1000, HP Inc. has developed an all-in-one desktop PC focused on collaboration as well as providing an immersive video experience with its stunning 34-inch display. The AIO includes a dual-facing pop-up webcam for videoconferencing, and video chats can be launched by pressing a key on the base of the PC. The massive display offers sharp and vivid picture quality with WQHD (2,560 × 1,440) resolution, along with a minimal bezel around the screen. And in terms of audio, the PC includes premium Bang & Olufsen speakers and HP Audio Boost technology (for balancing loudness and clarity). In addition, the EliteOne 1000 offers major horsepower with up to an Intel Core i7 processor and up to 32 GB of RAM.
Finalists:
Elo 02-Series of Touchscreen Monitors
Available in sizes ranging from 19 inches to 27 inches, Elo’s 02-Series of commercial-grade touch-screen monitors offer an edge-to-edge glass design, strong durability for continuous public use and the flexibility to attach up to four peripherals.
IGEL UD7 Universal Desktop Thin Client
The most powerful thin-client solution in IGEL’s portfolio, the UD7 features integrated AMD Embedded R-Series SOC with AMD Radeon R5 graphics, and also differentiates from the thin- client competition with management through the IGEL Universal Management Suite for automated control of IGEL endpoints.
Kensington SD7000 Surface Pro Docking Station
For use with Microsoft’s business-friendly Surface Pro line of devices, Kensington has introduced the SD7000 Surface Pro Docking Station. The station includes both docking/charging as well as locking for the 2-in-1 tablet, and can be used with either the fifth-generation Surface Pro model or the Surface Pro 4.
LG 38CB99-W 21:9 Curved UltraWide Monitor
A unique monitor solution for professionals such as web developers, analysts and traders, the LG 38CB99-W 21:9 Curved UltraWide Monitor offers QHD (3,840 x 1,060) resolution and dual-system connectivity, enabling users to share two PCs on one display simultaneously for work such as comparing data.

Power Management Technology
Winner:
Eaton Visual Capacity Optimization Manager
Eaton’s data center system optimization platform, Visual Capacity Optimization Manager, provides intuitive power management and business intelligence by monitoring the power infrastructure of both IT and facilities. Visual Capacity Optimization Manager reduces operational expenses for data centers and improves the reliability of systems and applications, while also using data analysis to help mitigate risk. Along with easily tracking usage, utilization and capacity limits and more, users are empowered to react quickly to address infrastructure concerns. Eaton’s Visual Capacity Optimization Manager lowers the total cost of ownership for critical infrastructure and presents major opportunities to provide customers with alternatives to manual monitoring.
Finalists:
CyberPower Medical-Grade UPS Systems
With its Medical-Grade UPS Systems, CyberPower offers reliable backup power to sensitive medical equipment in hospitals and other health-care facilities. The battery backup units are designed for use in patient care vicinities and are tested to UL 60601-1 testing requirements.
Datto Managed Power
Datto’s Managed Power surge suppressor is designed to enable monitoring and remote power cycling, with management via the cloud. Nonresponsive devices can be rebooted remotely with a single click. The MP60 includes 4,000 joules of surge protection, six outlets, two USB-A and USB-C ports and integrated Wi-Fi.
Power Distribution Inc.—WaveStar Infinity
Monitoring and metering solution for power distribution equipment, WaveStar Infinity from Power Distribution Inc. offers real-time data collection, advanced visualization and detailed alarming. The solution offers high degrees of accuracy that enable users to do fault detection, energy management and tenant billing with improved efficiency.

Printers
Winner:
Lexmark MC2425adw Color Laser MFP
Along with high-productivity capabilities and a comparatively compact footprint, Lexmark’s MC2425adw Color Laser multifunction device offers innovative features that businesses and solution providers will appreciate. The MFP offers print output of 25 pages per minute and scans at up to 50 pages per minute, with a quad-core processor to enable strong performance along with 1-GB memory drives. Lexmark has designed the MFP to enable faster serviceability for solution providers, and the unit is also engineered for durability with steel frames rather than plastic. Other standout features of the MC2425adw include on-board weather sensing that assesses environmental conditions and makes adjustments to ensure superior quality for prints, regardless of the climate.
Finalist:
Epson SureColor T3170 Desktop Wide-Format Wireless Inkjet
Epson’s SureColor T3170 is a wide-format wireless inkjet printer offering rapid print speeds—with A1/D-size prints in 34 seconds—along with auto-switching between 24-inch rolls and 11 x 17 cut sheet media, integrated Wi-Fi for wireless printing and a 4.3-inch LCD color touch screen for easier usage.
Security—Cloud
Winner:
Attivo Networks ThreatDefend
With ThreatDefend, Attivo Networks has enhanced its portfolio with new deception techniques designed to derail attacks targeting nontraditional surfaces, including the cloud. Attivo’s ThreatDefend solution uses decoys to provide organizations with alerts when attackers target their infrastructure. Recent enhancements offer expanded threat deception decoys and lures for container and serverless deployments, and cloud support is available for Amazon Web Services, Google Cloud Platform, Microsoft Azure and Oracle. ThreatDefend also includes centralized aggregation and correlation of attack information, as well as sharing of threat intelligence with Security Operations Centers for enabling automated incident response.
Finalists:
Bitglass Cloud Security
With its Cloud Security offering, cloud access security broker Bitglass delivers advanced data and threat protection for a range of cloud applications and services—including G Suite, Amazon Web Services, Office 365 and Salesforce. The offering’s hybrid architecture leverages artificial intelligence, proxies and APIs and doesn’t require deploying any agents.
BetterCloud Activity-Based Alerts
With Activity-Based Alerts, BetterCloud—maker of an operations management platform for major cloud application vendors such as G Suite and Dropbox—offers continuous monitoring of event-related activity for malicious or unauthorized activity, then provides automated responses to curtail security threats.
Dome9 Arc Platform
Dome9’s Arc Platform brings automation of security and compliance in public cloud infrastructure by combining policy automation with the security capabilities of Amazon Web Services, Microsoft Azure and Google Cloud Platform—resulting in a single tool for uniform management of security across multi-cloud environments.
Sysdig Secure 2.0
For organizations looking to secure cloud-native applications in a faster, more-detailed manner, Sysdig Secure 2.0 is a powerful offering that combines image scanning, runtime protection and forensics—enabling identification and blocking of threats along with enforcement of compliance requirements.
Security—Data
Winner: Forcepoint Dynamic Data Protection
Forcepoint Dynamic Data Protection continuously assesses risk and automatically provides proportional enforcement that can be dialed up or down. This capability is enabled through human-centric behavior analytics that understand interactions with data across users, machines and accounts. The product applies an anonymous and continuously updated behavioral risk score to establish a baseline of “normal” behavior of each end user on corporate or unmanaged networks. The company’s intelligent systems, informed by the individual risk assessment, then apply a range of security countermeasures to address the identified risk. With the industry’s first automated enforcement capability that dynamically adapts, Forcepoint Dynamic Data Protection frees up security analysts to focus on higher-value activities.
Finalist:
Seceon aiMSSP
An offering for detecting and responding to cyberthreats before the withdrawal of crucial data, Seceon aiMSSP is a fully automated platform providing MSSPs with detection, containment and elimination of threats—proactively and in real time.
Security—Email
Winner:
FireEye Email Security
FireEye reports that attackers are shifting to malicious URLs from malware—and the company has responded in kind with updates to its Email Security offering, which uses threat intelligence to surface major threats and remove low-fidelity alerts. Recent enhancements to the FireEye Email Security offering include the addition of machine learning and analysis to its URL detection platform. Other key features include detection of malicious credential phishing sites (PhishVision), a phishing detection plugin (Kraken) and an automated malware intelligence gathering system (Skyfeed)—along with FireEye’s cost-saving focus on providing only validated, quality alerts to security teams.
Finalists:
Cofense Phishing Defense Platform
Cofense’s Phishing Defense Platform goes beyond simply offering security awareness training to offer a suite of products for stopping phishing attacks. Offerings include PhishMe (for training workers with phishing simulations), Reporter (for easy reporting of suspicious emails) and Triage/Vision (for ingesting and analyzing reported emails).
Cyren Email Archiving
As a key capability of Cyren’s Cloud Security platform, Cyren Email Archiving provides essential capabilities such as rapid search and eDiscovery, tamper-proof email store and audited user access—dramatically simplifying email protection and management and meeting critical regulatory compliance standards.
Graphus
An offering that integrates with Office 365 and G Suite, Graphus provides automatic elimination of social engineering threats using patented artificial intelligence technologies and detection of attacks that have evaded other security controls. Threats addressed include spearphishing, phishing and business email compromise scams.
Mimecast Awareness Training
With a focus on changing the security culture within organizations, Mimecast’s Awareness Training platform helps to reduce human error in the workplace with security training videos to drive behavior change and risk scores on each user that are used to help target relevant content.
Security—Endpoint
Winner:
Sophos Intercept X
With the latest version of the Intercept X anti-exploit application, Sophos incorporates deep-learning technology to boost malware detection rates—making it the only product in the world to combine machine learning, malware and exploit blocking, and ransomware protections into a single offering. The addition of deep learning makes it possible for Intercept X to curate and label data even more accurately since it’s now able to process hundreds of millions of samples rather than just tens of millions of samples. As a result, Intercept X makes more accurate predictions at a faster rate with fewer false-positives when compared with traditional machine learning.
Finalists:
CrowdStrike Falcon X
CrowdStrike Falcon X automates threat analysis and helps deliver customized intelligence and Security Operations Center automation to large and small organizations. The solution combines malware sandboxing, malware search and threat intelligence into an integrated offering that can perform comprehensive threat analysis in seconds instead of hours or days.
Cybereason AI Hunting Platform
Cybereason’s AI Hunting Platform brings an automated approach to cybersecurity that includes artificial intelligence, behavioral analytics and machine learning to make hunting possible for all security professionals, regardless of skill level. Applying artificial intelligence to hunting allows organizations to figure out if they’re under attack without the overhead typically associated with hunting.
McAfee MVision Endpoint
McAfee MVision Endpoint is a completely new offering for Windows 10 designed to leverage the native Microsoft security capabilities of Windows Defender. Security settings can be managed from the company’s Software-as-a-service management offering, the ePolicy Orchestrator.
SparkCognition DeepArmor
With DeepArmor, which provides artificial intelligence-based endpoint protection, SparkCognition is aiming to do a better job of detecting advanced threats without creating performance issues—the result of DeepArmor not requiring daily or weekly scans along with getting regular updates.
Security—Identity Management
Winner:
CyberArk Privileged Access Security Solution v10
With version 10 of its Privileged Access Security Solution, identity and access management specialist CyberArk has upped its game on protecting organizations from the exploitation of privileged accounts, credentials and secrets. The comprehensive offering works by identifying and locking down credentials, and then continuously monitors for anomalous behavior. Recent enhancements in version 10 of CyberArk’s Privileged Access Security Solution include improved automation, enabling a dramatic reduction in time spent on privilege-related tasks and onboarding accounts. The latest version also adds new integrations that expand support for Amazon Web Services while bringing cloud-based analytics and machine-learning capabilities to CyberArk’s Endpoint Privilege Manager.
Finalists:
Bomgar Privileged Access Management
Bomgar’s Privileged Access Management offers a simple-to-understand, but powerful, offering for security. The offering changes privileged credentials as needed—as often as every hour—in order to thwart hackers from exploiting credentials, ultimately containing cyberattacks that penetrate a network.
ID Agent Dark Web ID
For MSPs looking to deploy compromised credential monitoring for their customers, ID Agent’s Dark Web ID solution provides both a simple user platform and sophisticated capabilities—bringing together intelligent monitoring with powerful search for identification of compromised emails and passwords.
Okta Identity Cloud for Security Operations
A solution for users of ServiceNow, Okta Identity Cloud for Security Operations provides an identity data feed to enable organizations to see context around user identity (such as summaries of user behavior) and to also manage security incidents inside the ServiceNow platform.
One Identity Safeguard
For managing the key aspects of privileged access—including storage, recording and analysis of access—One Identity Safeguard leverages automation to protect privileged accounts. The solution provides options between offering direct access to passwords or to recorded sessions, while also analyzing privileged activity for unusual behavior.

Security—IoT
Winner:
Fortinet FortiNAC
While the arrival of the Internet of Things is doing wonders for businesses in their quest for digital transformation, visibility into what is attached to networks has suffered—creating major security risks. With FortiNAC, Fortinet is meeting the challenge with a Network Access Control solution that provides full visibility into every user and endpoint, including IoT devices. The solution also provides capabilities for controlling those devices and users, while offering automated response to dramatically speed up the reaction time to events, and is highly scalable. FortiNAC offers 100 percent visibility into wired and wireless networks, enabling organizations to securely benefit from the IoT revolution.
Finalists:
Armis
With its agentless platform, Armis provides comprehensive discovery of all devices within an organization—including managed, unmanaged and IoT devices—while also providing behavioral profiling, sanctioning and automatic disconnection of any devices that are behaving questionably.
Claroty Platform
A solution for protecting operational technology such as industrial control systems and the industrial Internet of Things (IIoT), the Claroty Platform provides monitoring of all network communication along with the establishment of a high-fidelity baseline—providing context-rich alerts on malicious attacks.
Exabeam Entity Analytics
After setting a baseline for normal behavior, Exabeam’s Entity Analytics solution analyzes activity in device logs—with an eye toward uncovering suspicious behavior—and then presents security administrators with “watch lists” that enable them to isolate the problem or reconfigure the network if necessary.
ForeScout CounterAct
Enhancements in ForeScout’s CounterAct 8 include increased device visibility and control—including improved insight into fast-growing enterprise devices such as industrial and critical infrastructure devices—along with increased device intelligence (through analysis of crowd-sourced data) and improved scalability.

Security—Network
Winner:
WatchGuard AuthPoint
For organizations looking to bolster their network security capabilities with multifactor authentication, WatchGuard Technologies’ AuthPoint offers a compelling cloud-based approach that is specially tailored to small and midsize businesses (and the managed security service providers and other solution providers who serve them). The solution uses WatchGuard’s AuthPoint mobile app for authentication and allows organizations to view and manage login attempts through push notifications, one-time passwords or QR code entries. Common barriers to multifactor authentication that AuthPoint eliminates include complex processes for integration, large up-front investments and steep requirements for on-premises management.
Finalists:
Balbix BreachControl
Using advanced artificial intelligence capabilities, Balbix’s BreachControl offers predictive analysis of breach risks on a continuous basis. The solution automatically tracks all enterprise assets, whether or not the assets are managed, and offers a visual representation of the risk situation on a searchable heat map.
Meta NaaS
With Network-as-a-Service from Meta Networks, organizations are able to go beyond conventional VPN approaches by providing instant, secure remote access to applications as needed. The solution uses software-defined perimeters to enable identity-based, zero-trust access.
Pulse Secure—Pulse Policy Secure 9.0
For protecting applications in hybrid IT environments, Pulse Secure’s Pulse Policy Secure 9.0 simplifies the process with policy-based control. The offering includes on-demand VPN for Android devices; fully qualified domain name (FQDN) split-VPN tunneling for provisioning cloud access; and always-on VPN that offers improved control of internet traffic.
Webroot SecureAnywhere DNS Protection
With SecureAnywhere DNS Protection, Webroot offers Domain Name System security that is simple to deploy and works by automatically blocking access to questionable website domains prior to connections being made. The offering blocks malware prior to it even reaching an organization’s network.
Security—Threat Intelligence/Protection
Winner:
Recorded Future
Recorded Future offers breakthrough threat intelligence by pulling together data from a comprehensive set of sources across the open, deep and dark web—and then performing unprecedented analysis of the data to offer powerful and customized intelligence on cyberthreats. Recorded Future also stands out with its unified approach to threat intelligence—which provides centralized threat data in one dashboard display, eliminating the need for using disparate intelligence sources. The offering identifies threats more quickly—and identifies more threats overall—while enabling organizations to effectively integrate the information into their everyday security processes.
Finalists:
Infocyte Hunt
Infocyte Hunt simplifies the threat hunting process by reducing the skill set requirement for pursuing malware and advanced persistent threats. The product significantly reduces the period of time between infection and discovery—denying bad actors the ability to operate undetected.
Netskope Advanced Threat Protection
For detection of threats in Infrastructure-as-a-Service environments—along with reversal of malware and recovery from ransomware—Netskope’s Advanced Threat Protection brings together advanced heuristics, cloud sandboxing, threat intelligence, behavior analytics and machine learning to offer a comprehensive threat protection solution.
XM Cyber HaXM
HaXM is XM Cyber’s advanced persistent threat simulation solution, which delivers both realistic advanced persistent threat experiences and remediation. The HaXM platform takes the point of view of hackers in order to simulate, validate and remediate attack paths.
Security—Web/Application
Winner:
Netskope for Web
A leader in cloud security, Netskope is extending its protection of cloud environments to the web with its unified “one cloud” approach—bringing together cloud and web security into a single architecture. Netskope for Web features capabilities such as advanced threat protection, data loss protection, dynamic web classification, content filtering and real-time web analytics. Meanwhile, Netskope’s CloudXD capability provides an accurate view by identifying activity from actual users. The ability to secure both Infrastructure-as-a-Service and web environments from one security cloud provides major benefits in terms of streamlining security infrastructure, removing the need to juggle multiple disparate products.
Finalists:
Comodo Cybersecurity cWatch Web
Combining a web application firewall with analysis from a fully managed (and 24/7 staffed) Cyber Security Operations Center, Comodo’s Cybersecurity cWatch Web secures websites and applications with services including malware detection, prevention and removal.
Imperva Attack Analytics
By leveraging advanced artificial intelligence and machine-learning technologies, Imperva Attack Analytics takes massive numbers of application security events and distills them into highly readable security narratives—bringing simplicity to security investigations and enabling organizations to respond to threats more quickly.
Nutanix Flow
Nutanix Flow provides application-centric security to protect against internal and external threats that are undetected by traditional perimeter-oriented security products. As enterprises are turning to cloud-based infrastructure for modern business applications, protecting the application requires micro-segmentation capabilities such as those offered by Nutanix Flow.

Servers
Winner: Dell EMC PowerEdge MX
With PowerEdge MX, Dell EMC offers a future-proof composable architecture featuring high performance, modular computing, storage and networking infrastructure. The PowerEdge MX differentiates with the ability to provide customers true server disaggregation and full composability that can deliver cloud-level velocity. The “kinetic infrastructure” of the PowerEdge MX extends the flexibility of configuration down to the individual storage device and, eventually, all the way to memory-centric devices. Importantly, PowerEdge MX is managed by Dell EMC's OpenManage Enterprise Modular Edition system engine, which enables life-cycle management on all PowerEdge MX components including storage, compute and networking across multiple chassis at once.

Storage—Cloud
Winner:
IBM Cloud Object Storage
While aimed at organizations looking to store massive amounts of data in public cloud environments—up to exabyte scale—IBM Cloud Object Storage has expanded its capabilities over the past year to serve organizations that are looking to start at a smaller scale, with a 72- TB starting object storage configuration. The solution offers impressive durability and availability, along with meeting crucial compliance standards. IBM Cloud Object Storage also stands out with a large number of certified solutions—77—that can be integrated together with it, as well as by offering 10 percent less storage overhead in standard configurations.
Finalists:
Infinidat Neutrix Cloud
With its Neutrix Cloud block and file storage-as-a-service, Infinidat offers multi-cloud and hybrid cloud flexibility—supporting Amazon Web Services, Microsoft Azure, Google Cloud Platform and VMware Cloud on AWS—along with strong availability and features such as InfiniSnap snapshot integration.
Qumolo QF2
Qumolo QF2 offers easy scaling of data across on-premises environments and Amazon Web Services, bringing file-based data with billions of objects to the cloud. The solution is built on Qumolo’s cross-cluster replication technology, which allows data to be moved where it is needed, as it is needed.

Storage—Enterprise
Winner:
Dell EMC PowerMax
Dell EMC’s PowerMax all-flash arrays, formerly known as VMAX, offer a complete architecture refresh of the prior offerings built from the ground up to be ready for the latest storage media technologies—including new NVMe flash storage and future storage class memory. PowerMax is targeted at next-generation applications such as real-time analytics, genomics, artificial intelligence, IoT and mobile applications. The arrays implement machine learning to improve performance and provide proactive system health monitoring. The PowerMax 2000 scales to up to 1 petabyte of effective capacity, with up to 1.7 million IOPs of performance, while the PowerMax 8000 scales to up to 4 petabytes of effective capacity, with up to 10 million IOPs of performance.
Finalists:
HPE 3Par Storage
Along with offering stunning performance and scalability—with the ability to start at 4 TB and seamlessly expand to 20 PB in a single system—HPE 3Par now includes Nimble InfoSight predictive analytics for predicting storage issues and proactively resolving them before they impact the installed base, powering dramatic reductions in total cost of ownership.
IBM FlashSystem 9100
With FlashSystem 9100, IBM has introduced its first storage system featuring embedded high-performance NVMe storage capacity. The offering supports both IBM’s proprietary FlashCore flash storage modules as well as industry-standard SSDs, and comes with Storage Insights, IBM’s artificial intelligence-powered analytics software.
Nexsan Assureon Cloud Transfer
With Assureon Cloud Transfer, a recently introduced feature of Nexsan’s Assureon secure archive storage system, data can be more easily migrated or copied to and from public cloud platforms to Assureon’s on-premises archive storage—enabling improved data protection and retention over the long term.
Western Digital IntelliFlash
With its N-Series IntelliFlash arrays, Western Digital is offering high-performance NVMe flash storage that’s targeted at real-time transactional applications, machine learning and deep analytics. The line ranges from an entry-level model—with raw capacity starting at 23 TB—to the highest-end array featuring up to 1.26 petabytes of raw capacity.

Storage—Midrange
Winner:
HPE Nimble Storage Flash Arrays
Hewlett Packard Enterprise’s latest Nimble Storage Flash Arrays are designed to take advantage of both NVMe flash storage and storage-class memory and are backed by an HPE guarantee to deliver the best storage efficiency of any all-flash array. The all-flash arrays also include a 99.9999 percent guaranteed availability along with the company’s InfoSight predictive analytics—enabling solution providers to quickly pinpoint application performance IO bottlenecks. In addition, they allow hybrid and secondary flash technology in a single array, support inline variable deduplication, and scale up to a high-end model with 4 petabytes of storage capacity at less than 1-millisecond latency.
Finalist:
IBM Storwize Family
For business groups with entry to midsize applications—but that still need a range of business-critical features—the IBM Storwize family provides enterprise-class system availability and data security, including powerful data migration and remote mirroring capabilities that leverage IBM’s HyperSwap technology.
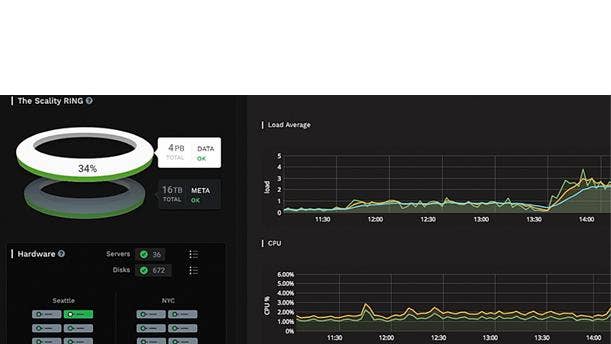
Storage—Software-Defined
Winner:
Scality Ring
With major advancements to ease of deployment and operation—as well as entry-point affordability—Scality’s 7.4 release of its Ring offering brings its software-defined prowess to the next level. A developer of distributed file and object storage technology, Scality offers its Ring software-defined storage solution industry-standard hardware platforms. With the 7.4 release, Ring is available in new three-server configurations for HPE Apollo 4200/4510—enabling a more affordable path into scale-out software-defined storage. Meanwhile, ease-of-use upgrades include offering a simplified window into monitoring and management of servers (using the new Ring Supervisor UI), along with faster deployment through a new unified Installer.
Finalists:
DataCore PSP7 Release
Updates in DataCore’s PSP7 release of its software-defined storage and hyper-converged virtual SAN include patented technology for overcoming I/O bottlenecks and inefficiencies—delivering maximum performance, uptime and utilization of resources. Key functionality includes multi-way mirroring to enhance continuous availability and scale-out resiliency in storage systems.
Hedvig Distributed Storage Platform
Aimed at enterprises building private, hybrid or multi-cloud environments, Hedvig’s software-defined Distributed Storage Platform stands out by being designed for both primary and secondary data. The solution—a good option for virtualized, containerized and backup workloads—consolidates block, file, and object into a single API-driven platform.
NexentaCloud
The NexentaCloud solution for Amazon Web Services offers rich data storage leveraging the NexentaStor enterprise software-defined storage platform—providing enhanced storage efficiency for public cloud through data reduction, improved visibility and, ultimately, better management of cloud workloads.

Editor’s Choice
Winner: HP Jet Fusion 300/500 Series 3D Printers
HP Inc.’s 300 Series and 500 Series Jet Fusion 3-D printer models feature the same technology as the company’s production part 3-D printers, but with a smaller footprint and a focus on printing prototypes. The expanded Jet Fusion lineup includes models that can print full-color objects as well as models that just do black-and-white. Capabilities include printing at high speeds—up to 52 parts in 15 hours. The latest Jet Fusion 3-D printers also differ from the original models by having a more compact size—they are all-in-one machines, in comparison to the three systems of the original Multi Jet Fusion—helping to allow Jet Fusion 3-D printing technology to reach a broader set of customers.
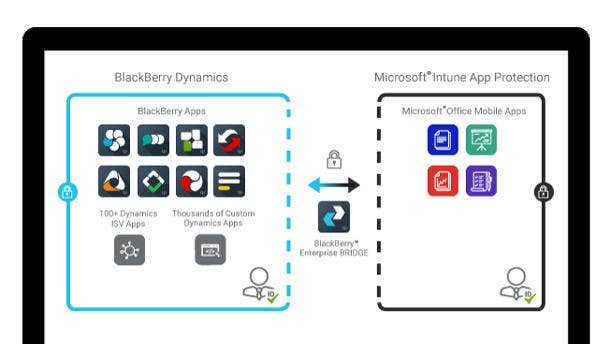
Editor’s Choice
Winner: BlackBerry Enterprise Bridge
As part of a strategic partnership with Microsoft, BlackBerry has developed its Enterprise Bridge solution that enables seamless use of Microsoft mobile apps from within the BlackBerry Dynamics secure container. Joint customers of the two companies, such as government agencies and health-care providers, can thus benefit from Enterprise Bridge as a highly secure option for using Microsoft’s Office 365 suite of apps such as Excel, PowerPoint and Word. The offering provides both assurances about security and privacy of critical corporate data along with helping customers to meet regulatory requirements.