12 Big New Network And Endpoint Security Tools From The Black Hat 2019 Conference
Here's a look at 12 products released during the Black Hat 2019 conference that turn network assets into security devices, redirect attempted endpoint access into deception environments, and use machine-learning algorithms on network flows.

Protecting The Core
Vendors attending the Black Hat 2019 conference have placed big bets around network and endpoint security, debuting offerings that turn network assets into security devices, redirect attempted endpoint access into deception environments, and use machine-learning algorithms on network flows and packet data.
Cybersecurity companies have doubled down on everything from identifying emerging DDoS and botnet threats to ensuring consistent policies across cloud and IoT environments to investigating attacks against Windows or Linux-based servers.
Behavioral analytics has played a key role in moving the ball forward, with vendors creating behavior baselines for evePry device and machine and working to prevent anomalous or malicious user behavior. Here's a look at what 12 Black Hat 2019 conference network and endpoint security vendors are doing to reduce the attack surface, investigate incidents, and pre-empt attacks before they escalate.
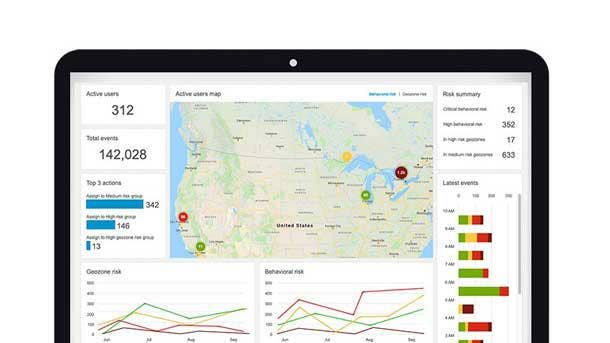
BlackBerry Intelligent Security
BlackBerry Intelligent Security leverages the power of adaptive authentication and AI-driven security to create a more secure, contextual system for unified endpoint management. It solves dynamic threat landscape challenges by intelligently driving security policies across endpoints based on risk and the context of actions being performed in real time.
The product enforces security by detecting and preventing anomalous and malicious user behavior according to an organization's regulatory and security policies. BlackBerry Intelligent Security utilizes a range of personal identifiers and capabilities to seamlessly secure endpoints across financial services, government, transportation, professional services and other industries.
BlackBerry Intelligent Security uses AI to accommodate employees' workflows and maintain security protocols that otherwise might be compromised by well-intentioned workarounds. And machine- learning capabilities enable the system to identify the behavioral and locational patterns of multiple users to determine risk and grant the appropriate access.

Gurucul Network Behavior Analytics
Gurucul Network Behavior Analytics identifies unknown threats by using advanced machine-learning algorithms on network flows and packet data. The tool creates behavior baselines for every device and machine on the network based on network flow data, and leverages logs to correlate IP-specific data to machines and users.
The product comes with prepackaged machine-learning modules tuned to run on high-frequency network data streams to detect real-time anomalies and rank risk threats. The use of linked data and threat models allows Gurucul Network Behavior Analytics to identify advanced and unknown threats like zero-day exploits, fileless malware and ransomware.
The product does this by detecting unusual behavior on a server or device, related lateral movement within the network, command and control communication, access misuse, and suspicious account activity from a compromised account. The product's data processing and analytics framework can uncover stealth operations that lie dormant between various stages of a cyberattack.

Netography Distributed IPS
Netography Distributed IPS (Intrusion Prevention System) addresses the disappearing network perimeter by turning any network asset into a security device. Its use of cloud-native infrastructure and distributed telemetry gathering allows workers to discover, investigate and remedy modern threats with speed and autonomy.
The product continuously and automatically detects and remediates malicious traffic, and works by ingesting all common flow data via a proprietary cloud flow collector. The flows are monitored by a host of proprietary algorithms, which can trigger plugins capable of doing anything from re-routing networks to defending global infrastructure.
Unlike on-premises IPS devices that lack unlimited storage and compute capacity, Netography Distributed IPS can discover extremely complex security events that typically go unseen. The tool is complementary to existing security deployments, and enables teams to better control devices and reduce threats.
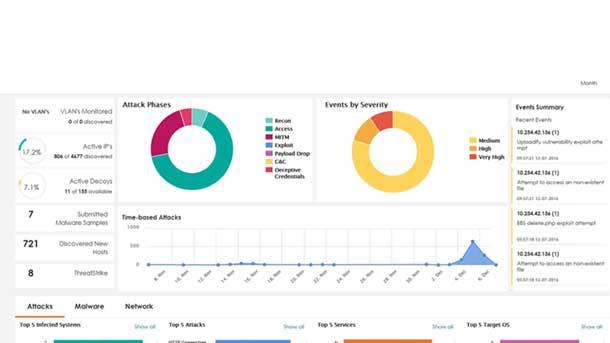
Attivo Networks ThreatDefend Platform
New capabilities on the Attivo Networks ThreatDefend Platform monitor available services on production endpoints and redirect attempted access into a deception environment. Every endpoint on the network becomes a decoy and, when paired with Attivo's deception lures, locks down an attacker's ability to break out from the endpoint without getting caught.
As a result, defenders gain visibility into the attacker's tools, the use of malicious software, and attempted lateral movement, and are able to quickly quarantine infected systems. Creating a deception blanket over the endpoint ensures cybercriminals can't bypass or avoid detection regardless of the attack method they ultimately choose.
ThreatDefend Platform doesn't require agents on the endpoint or disruption to network operations, Attivo said. Attackers on average take just four and a half hours to move off an initially compromised system, making it critical to stop lateral movement so that the adversary can't establish a foothold.

Endgame For macOS
Endgame for macOS makes it easy for security analysts to triage alerts, investigate incidents, contain and control devices with a single click, and include all devices in their threat hunting operations. This comes a year after the company released an autonomous, tamper-resistant agent to protect online and disconnected Mac endpoints from attack.
The product offers machine-learning-powered malware prevention for known and unknown threats that has achieved a 99 percent block rate and zero false positives. Endgame for macOS also offers a large breadth of response actions such as automated file quarantine, kill process, file commands, and kernel-level hosted isolation of an endpoint.
Endgame for macOS has a single, lightweight agent to streamline administration management, enhance IT operations visibility, and optimize security incident response. The product also allows businesses to define their own real-time prevention, detection, and response actions to enforce compliance.
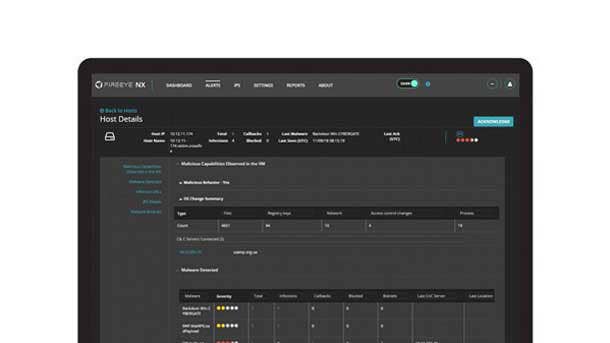
FireEye Network And Endpoint Security
FireEye Network Security 8.3 and FireEye Endpoint Security 4.8 allow for enhanced detection and investigation of advanced attacks against Windows or Linux-based servers. As a result, customers can more quickly investigate and triage lateral threats at the first sign of a breach, whether the servers are based on-premises, in the cloud, or in a hybrid environment.
Web shells, ransomware, cryptomining, botnets and shell scripts all enable attackers to keep a low profile in the system until they are ready to execute their attack. Getting visibility into the early stages of the attack life cycle is critical to protecting business infrastructure, FireEye said.
The latest updates to FireEye Network Security and FireEye Endpoint Security allow organizations to detect, investigate and remediate advanced attacks in days or hours rather than weeks or months. For instance, security practitioners using FireEye can detect web shell-based attacks within minutes and quickly respond by containing the server, webpage or app.

Fortinet E-Series FortiGate Next-Generation Firewalls
Fortinet's new E-Series FortiGate Next-Generation Firewalls support security-driven networking and enable organizations to securely accelerate their on-ramp to the cloud. The E-Series makes it possible for customers to deliver seamlessly integrated end-to-end security through offerings such as Secure SD-WAN from branch locations and high-performance secure connectivity through data centers.
The FortiGate 1100E, FortiGate 2200E and FortiGate 3300E solve some of the most common bottlenecks enterprises face when trying to secure connect to the cloud, including achieving secure, high-speed connections to multiple clouds and providing perimeter defense and DDoS protection.
The FortiGate E-Series also excels at delivering full visibility into encrypted flows, segmenting the network, and protecting business-critical applications and servers. The new lineup accelerates the cloud on-ramp with optimal user and application experience and features, and offers a variety of price points, interfaces and performance levels to meet the diverse needs of enterprise data center deployments.
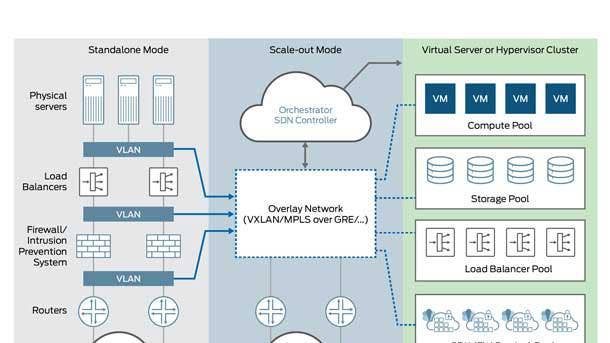
Juniper cSRX Containerized Firewall
The cSRX extends security to where cloud-native applications reside, ensuring consistent policy across private cloud, public cloud and IoT infrastructures. The product allows for containerization of the network to align with the customer movement of applications and services from physical to virtual to containers.
The cSRX simplifies management from an application team's perspective since it's merely a waypoint in networking and the policy is transparent.
The product can be integrated with traditional security management and software-defined networking controllers such as Tungsten Fabric or Juniper's Contrail. For instance, Juniper said the integration of cSRX with Contrail fortifies micro-segmentation with deeper universal threat management.

Check Point 16000, 26000 Security Gateways
Check Point Software Technologies’ new high-end appliances are intended to serve data center and telecom environments. The 16000 Base, 16000 Plus and 26000 Turbo are extensions of the company's new security gateway appliance series, and incorporate Check Point's ThreatCloud and SandBlast Zero-Day Protection. They can be ordered immediately and are scheduled to be shipped by September.
The new appliances are intended to help organizations safely and efficiently adopt cloud technologies as part of their digital transformation, according to Check Point CEO Gil Shwed. The 26000 Turbo offers 30 Gbps of advanced threat protection, 316 Gbps of firewall throughput, and a fully redundant power supply and storage configuration.
The 16000 Plus, meanwhile, offers 12 Gbps of advanced threat protection, 159 Gbps of firewall throughput, and a fully redundant power supply and storage configuration. And the 16000 Base provides the flexibility to tailor the network, storage and power supply configurations, and has the same form factors and performance as the 16000 Plus.
CrowdStrike Falcon Summer Platform Release
CrowdStrike Falcon's summer platform release is packed with new innovations focused on helping security organizations execute their missions with the high speed and efficiency. Tailored intelligence enables real-time identification of emerging DDoS and botnet threats that target an organization.
Meanwhile, instant visibility into external threats enables security teams to act and remediate faster than ever before, avoiding significant impact and possible downtime. And custom indicators of attack provide customers with the ability to quickly and easily create and fine-tune custom behavioral threat detection to gain real-time visibility into suspicious behaviors.
The latest CrowdStrike Falcon release allows users to remotely connect to macOS hosts and run predefined commands to immediately respond to and remediate threats as they happen. And the ability to collect information, place and retrieve files, run scripts, and execute remediation commands across multiple hosts simultaneously dramatically increases efficiency and improves time-to-response.

Attivo Networks Active Directory
Attivo Networks Active Directory intercepts advanced attacks and contains them automatically at the endpoint. When Active Directory queries are made, the response gets altered and deceptive content is added, creating an altered reality for the attacker.
As a result, Attivo said the attack surface is reduced and valuable enterprise resource information can be more easily hidden. The redirection of activities into the deception environment allows for the safe gathering of the attack's tactics, techniques and procedures, as well as company-specific threat intelligence.
Active Directory can be purchased stand-alone or as part of the ThreatDefend Endpoint Suite.

CyVent-Deep Instinct Endpoint Prevention
Companies working with CyVent can now leverage Deep Instinct's deep learning predictive capabilities to ensure multilayer protection across all endpoints, servers, mobile devices and operating systems. The advent of deep learning is a real game-changer, making it possible to move the needle back to pre-empting attacks before they execute.
The partnership provides multiple layers of protection, including predict and prevention followed by detection and response. Customers can expect on-device, zero-time protection even if there's no internet or network connection.
The integration allows for file-based and fileless threat detection, including around zero-days, advanced persistent threats (APTs), macros, scripts, and code injections. And the tool functions quickly and seamlessly without any impact on user experience.