13 Android Security Attacks To Watch

Android Security Attacks: The Dark Side Of Smartphones
Malware authors are painting with a bigger palette these days. The gaping Google Android platform, giving legitimate developers license to flex their creative muscles, has also served a similar purpose for cyber hackers aiming to execute malicious attacks.
Subsequently, the security landscape is replete with fresh waves of malware written specifically for the Android platform. Like malware written for the PC, Android threats are rapidly becoming more creative and targeted, reeling in victims by impersonating surveys, Android games and other legitimate applications. But once downloaded, users are subjected from everything to an embarrassing SMS blast to information stealing malware that silently lifts login credentials, bank account numbers and other sensitive information.
Here are a few of the Android security attacks that have made the biggest splash.

HolyColbert
Like the Comedy Central comedian, this Android attack dubbed HolyColbert, appears to have a sense of humor. Adding to the snarky sense of comedy is the tie-in date of May 21, 2011, the alleged ’end of the world’ perpetuated by some media sources. On this date, the malware began automatically replying to SMS messages sent to infected devices with the following text: ’Cannot talk right now, the world is about to end.’ The malware then Trojaned a legitimate, if controversial, free application called the ’Holy F***ing Bible,’ before randomly selecting one of several other similar anti-Christian messages and proceeding to text them to everyone on the victim's contact lists. Meanwhile, the malware also changed the devices' wallpaper, sent the user’s e-mail and phone number to a remote website and contacted the command and control server every 33 minutes. The attack also subscribed users to a mailing list related to the Colbert Report. Officially known as the Android/smspacem.Altr, the attack targets mobile devices running Android 2.1 or greater.
(Image provided by Symantec)
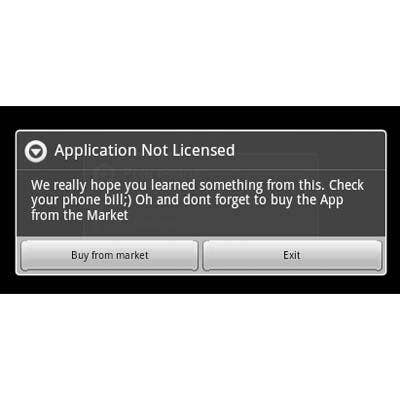
Walk And Text
The Android Walkinwat malware masks itself in infected versions of "Walk and Text,’ in a type of attack known as "Shameware,’ which sends a message or attempts to compel action by publicly embarrassing the user. During the Walk and Text attack, the malware reads through the contacts on the user’s Android mobile device in order to blast out a humiliating SMS message pointing out that the app the user has downloaded is in fact a cheap, pirated copy. Coupled with the text message blast, the attack will also display a dialog to the user, insulting him or her for downloading a pirated app. The intention of the attack is an oblique attempt to shame the user into purchasing the legitimate app.
One text message reads: Hey, just downloaded a pirated App off the Internet, Walk and Text for Android. I’m stupid and cheap, it only costs 1 buck. Don’t steal like I did.
(Image provided by Webroot)
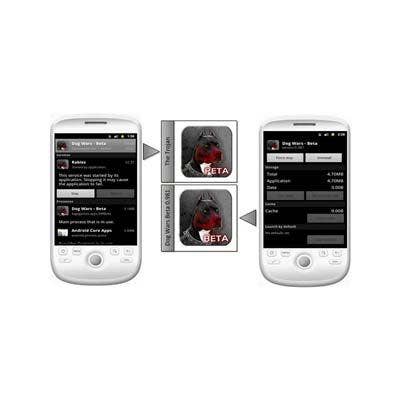
Dog Wars-Beta
Similar to the Walk and Text threat, this attack is designed solely to send a political message and shame the user. During this Android Trojan attack, users are asked to grant permission to install an app on their phone that purports to be the Android game Dog Wars. Once installed, the display icon of the bogus Dog Wars app bundled with the Trojan appears almost identical to that of the legitimate app. However, one small difference is that the icon of the malicious app reads PETA instead of BETA. The Trojan code is then injected as a package called Dogbite. Once the infected device starts up, a service called, ’Rabies’ launches in the background. As the Rabies service is executed, it sends out a text message to everyone on the contact list of the user's phone that read ’I take pleasure in hurting small animals, just thought you should know that.’ The attack culminates by sending an SMS message to 73822 with the word ’text,’ which is an attempt to sign up the compromised device to a text/alert service operated by PETA.
(Image provided by Symantec)
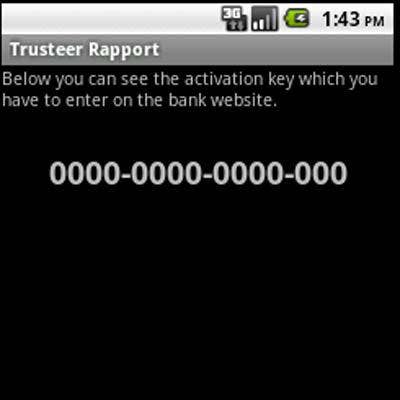
Zitmo
The Android SMSSpy, or Zitmo, was found in a fake Android application appearing to be from Trusteer, a security firm which ironically does not have an Android security solution. Zitmo, an acronym for Zeus in the Mobile, has now been written to run on the Android system, expanding the platform past Windows Mobile, Symbian and Blackberry operating systems.
At its core, Zitmo operates as a man-in-the-middle attack by intercepting two-factor authentication that banks use to validate the identity of the account holder when entering login credentials, typically with a one-time password that is sent to a mobile device via SMS. During the attack, the malware essentially lifts SMS texts containing bank account passwords and other sensitive information sent to the user, which are then promptly funneled to a remote server. Even if a particular bank doesn’t require two-factor authentication, Zitmo can forward and spy on all SMS messages, making it a valid threat.
(Image provided by Webroot)

Droid Kung Fu
This piece of Android attack, which targets mobile phones running Android 2.0 or greater, connects infected phones to a remote server. Once compromised, the users’ Android device will have the ability to follow commands imposed by the command and control server, including uninstalling a given package, downloading a malicious package and installing it, opening a malicious URL in the phone’s browser and running an infected application. The infected phone also reports some personal and system data back to the same server, including whether the phone is rooted or not, te OS type, SDK version, and available memory on the SD card, among other things. This malware has been reported on unofficial Android markets.
Fake Security
The Fake Security tool is in reality a Trojaned version of the Google Security tool released to combat the DroidDream Malware outbreak within the Android Market. This version was not available in the official market but rather in alternative Chinese markets. Like many attacks, it has the ability to send SMS messages when contacted by a remote command and control server.
(Image provided by Kaspersky Lab)
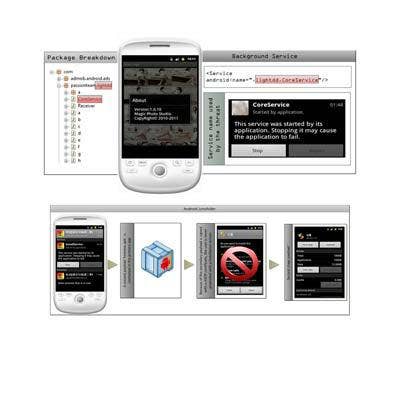
Android.Lightdd and Android.Jsmshider
Android.Lightdd and Android.Jsmshider are two Android malware threats that open back doors on infected devices. The attacks are unique in that they borrow a staged downloader strategy from traditional PC malware in an attempt to complicate infection to the point where a user can’t uninstall the malicious apps.
(Image provided by Symantec)
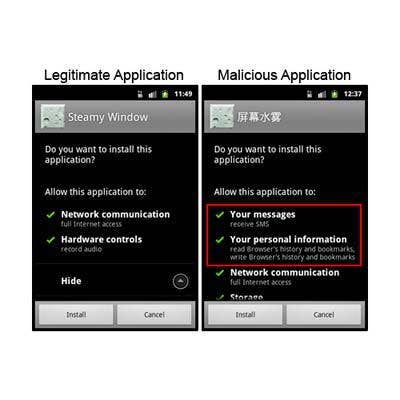
PJ Apps
Like most other Android Trojans, the Android PJ Apps Trojan spreads via altered versions of legitimate apps hosted on unregulated third-party Android marketplaces. In an effort to entice potential victims, the malware masquerades as the popular ’Steamy Window’ app. However, while the malicious app features some of the same capabilities as the original, it comes equipped with additional functionality that allows an attacker to build a botnet. Among other things, the malware has the ability to install applications, navigate to websites, add bookmarks to the user’s browser, send text messages and block text message responses. It also sends sensitive user information stored on the Android device back to the attacker. In light of its threat capabilities, researchers believe it was designed and may be used to peddle ad campaigns and to obtain benefits from the use of third-party premium rate services at users’ expense.
(Image provided by Symantec)
Autosub SMS
This Android attack, known as Androidos Autosubsms.A, is a Trojanized version of an app found on third-party app stores in China. Specifically, the Android malware monitors text messages and abuse premium services, as well as specific key words in text messages in order to subscribe affected users to a premium service without their consent, subjecting them to unexpected charges.
(Image provided by Trend Micro)
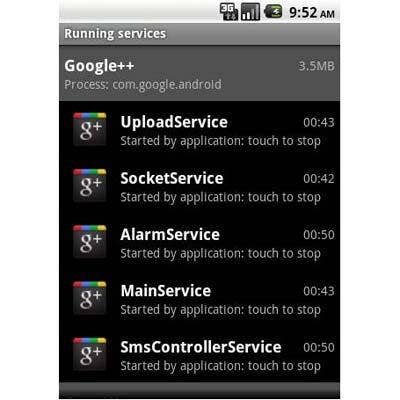
Nicki Spy
Known as Nicki Spy, this Android malware lures victims by posing as an invite to Google’s new social network Google+. However, once installed, the Nicki Spy Trojan performs an array of malicious functions that can also be used to conduct espionage activities, such as collecting text messages, call logs and GPS location from infected devices. All lifted communications are then uploaded to a certain URL through port 2018. The Android malware also has the ability to receive command via text messages, record phone calls made from infected devices and answer incoming calls automatically.
(Image provided by Trend Micro)
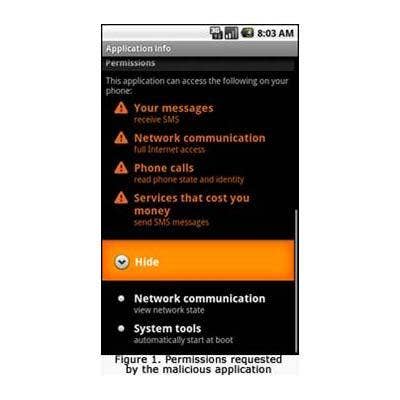
Lovetrap
This Android malware, called Lovetrap, disguises itself as a love test app, an e-book reader or a location tracker. It then proceeds with its malicious activities by retrieving the affected users’ International Mobile Subscriber Identity (IMSI) and sending it to a certain URL. The malware also sends out text messages to subscribe to certain unsolicited services, which in turn, accrue unwanted charges for the affected user.
(Image provided by Trend Micro)
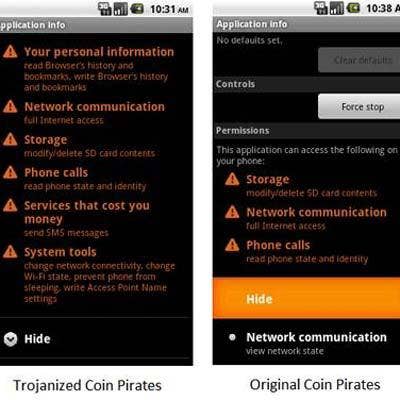
Coin Pirates
Trojanized versions of Coin Pirates app, also known as ANDROIDOS_PIRATES.A, were found on Chinese third-party app stores that steal information from users, such as device model, IMSI number and IMEI number from the infected device. It also connects to a specific server to download data.
(Image provided by Trend Micro)
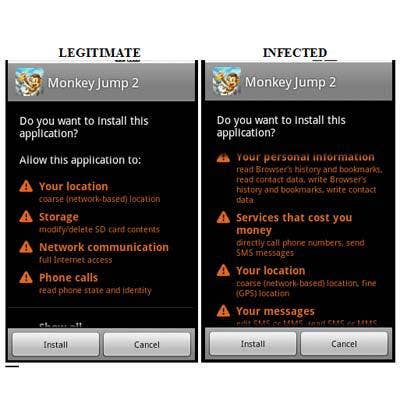
Android.Geinimi
Known as the Android Geinimi, this threat is found in infected legitimate applications, and widespread in third party Android app markets. Prior to install, the malware requests more permissions than the legitimate application to access greater Android functionality. Once installed, the malware proceeds to capture personal data and send it to remote servers controlled by cyber criminals. Like many Android attacks, it also comes complete with bot capabilities so it can receive command and control commands.
(Image provided by Webroot)