The 10 Coolest Cloud Security Tools Of 2021
The 10 coolest cloud security tools to hit the market in 2021 can block reverse shell attempts and cryptomining, help developers spot open S3 buckets, and protect workloads and applications hosted in public clouds.

Containing Cloud Threats
Read the latest entry: The 10 Hottest Cloud Security Tools and Products of 2022
Vendors have made great advances in 2021 around securing cloud applications, data, and workloads, rolling out tools that can block reverse shell attempts and cryptomining, help developers spot problems such as open S3 buckets, and visualize and prioritize cloud security risks to reduce the attacker’s blast radius and facilitate faster investigations.
Fostering more cloud visibility and collaboration has been a major area of investment, with companies delivering indicators of attack for the cloud control plane and extending zero trust security to workloads and applications hosted in public clouds. Other vendors, meanwhile, have focused on enable cloud-based data and intelligence sharing across security and IT operations teams.
Five of the coolest new cloud security tools come from companies based in California, three come from companies based in the Northeastern United States, and companies based in Michigan and Romania each contributed one offering to the list. Read on to learn what new cloud security features and functionality partners are now able to enjoy.

Aqua Platform
Aqua Security in July debuted a new cloud-native application protection platform (CNAPP) to ease the journey from scanning and visibility to workload protection in cloud-native environments. The platform reduces administrative burden and allows security teams to start with scanning and cloud security posture management, and then add in sandboxing capabilities and workload protection as needed.
The unified approach lowers management overhead for advanced runtime features and is available as a SaaS or self-hosted deployment, according to Burlington, Mass.-based Aqua Security. It also enables customers to benefit from better context and prioritization in identifying risks and threats and adopt a full life-cycle approach to securing cloud-native applications.
The Aqua Platform enhances runtime protection with file integrity monitoring for containers as well as threat response policies that specifically block reverse shell attempts and cryptomining. The platform can also define custom severities for specific vulnerabilities to conform with customers’ internal standards, according to Aqua Security.

Bitdefender GravityZone Security For Containers
Bitdefender GravityZone Security For Containers was introduced in July to provide threat prevention, extended endpoint detection and response and anti-exploit protection for containers running in private and public clouds. It can prevent, detect, and remediate threats against cloud workloads, including those made against Docker and Kubernetes containers, according to the Bucharest, Romania-based company.
GravityZone Security for Containers protects containers and cloud-native workloads against Linux kernel, application zero-day and known exploit attacks in real time, identifying which images and pods were involved in an incident. It eliminates Linux security compatibility challenges via a single, lightweight agent that enables companies to update Linux distributions faster without sacrificing security efficacy.
The product is multiplatform and provides complete security visibility and controls over all containers and workloads across hybrid or multi-cloud environments from a single dashboard, Bitdefender said. It also maps cloud workload container attacks to the MITRE ATT&CK Framework, detecting 100 percent of attack techniques against Linux systems in the most recent MITRE ATT&CK test, the company said.
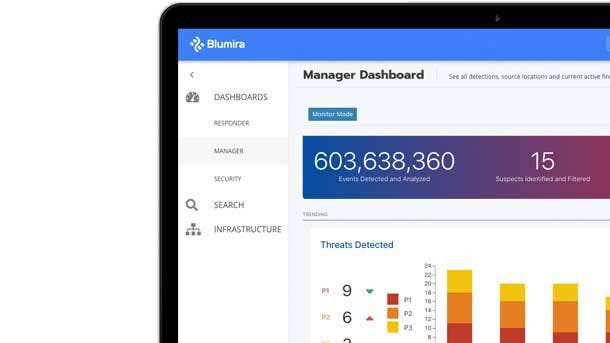
Blumira Cloud Collector
Cloud Collector debuted in August to help IT administrators set up integrations within Blumira more quickly and easily, connecting to cloud services like Amazon Web Services, Microsoft 365, Azure and Duo Security through APIs. The new proprietary detection system delivers real-time threat notifications in a matter of milliseconds so that IT staff can respond early enough to minimize the impact of an attack.
Ann Arbor, Mich.-based Blumira is also releasing new visualized security reports for Windows, Azure and Active Directory to help administrators gain more visibility and insight into their environment at a glance. This is expected to make it easier for administrators to quickly triage or investigate incidents further, according to Blumira.
The company said it offers the fastest time to deployment with broad cloud coverage, enabling organizations of all sizes to detect and respond to cloud security threats five times faster than the average SIEM provider. Blumira automatically provides ongoing parsing support for many different data types, saving customers a substantial amount of development time.
CrowdStrike Falcon Horizon
New Falcon Horizon features unveiled in May leverage CrowdStrike’s telemetry to deliver indicators of attack for the cloud control plane and provide DevOps tools for faster detection and remediation. The new capabilities include continuous threat detection, and monitoring and correlation across cloud and on-premises environments to help security teams cut through the noise of a multi-cloud environment.
Falcon Horizon’s new CrowdStrike Confidence Scoring continuously aggregates, assesses, and scores cloud control plane threats and changes in configuration to accurately identify malicious activity. The scores help security teams prioritize the most urgent threats, allowing them to identify, understand and act against critical threat activity and avoid sifting through inconsequential alerts.
Falcon Horizon enables faster integration and remediation with organizations’ DevOps and collaboration tools, seamlessly onboarding new cloud accounts through Sunnyvale, Calif.-based CrowdStrike’s API. The offering also provides simplified management and security policy enforcement from a single console, eliminating blind spots, preventing security incidents, and ensuring application availability for any cloud.
IBM Security Hybrid Cloud Blueprint
The IBM Security Hybrid Cloud Blueprint helps organizations modernize their security program with visibility and control over the most sensitive data and activities as they migrate to the cloud. The blueprint makes it possible for organizations to enable continuous compliance, reporting and response, monitor for cloud misconfigurations, and build consistent policy enforcement across all cloud workloads.
As part of this blueprint, customers can choose to purchase IBM Security Services for Cloud, which offers an open, automated approach to help simplify hybrid cloud security. The Cambridge Mass.-based business unit introduced this offering in May, which brings together cloud-agnostic security expertise together with an integrated set of cloud, proprietary and third-party technology solutions.
Meanwhile, IBM Cloud Pak for Security now combines leading capabilities in threat management and data security into a single, modular, easier to consume offering. And the new IBM Cloud Pak for Security as a Service provides access to a unified dashboard across threat management tools, with the option to easily scale with a usage-based pricing approach.

McAfee Enterprise MVision Private Access
McAfee Enterprise MVision Private Access was introduced in August to enable granular zero trust access to private applications hosted in public or hybrid cloud environments from any location or device. It offers integrated data loss prevention and threat protection capabilities for securing access and data collaboration around zero trust network access (ZTNA), according to the San Jose, Calif.-based company.
MVision Private Access provides complete coverage across managed and unmanaged devices and performs continuous risk assessment by deriving enhanced device posture information through McAfee’s endpoint security technology. It also works in conjunction with MVision Unified Cloud Edge to provide visibility and control across cloud, private applications, web and endpoints, the company said.
MVision Private Access enables advanced threat protection and complete control over data collected through private access sessions, preventing inappropriate handling of sensitive data and blocking files with malicious content. It also creates software-defined perimeters to provide limited access to applications based upon the user and device entitlements, preventing the lateral movement of threats.

Netskope Cloud Exchange
Netskope Cloud Exchange was unveiled in November to enable cloud-based data and intelligence sharing across security and IT operations teams to help them act faster and more effectively. New or enhanced integration modules are intended to help customers export logs, automate service tickets, share indicators of compromise (IOCs), and exchange risk scores, Santa Clara, Calif.-based Netskope said.
The Cloud Threat Exchange (CTE) enables automated bi-directional indicator of compromise (IOC) sharing of file hashes and malicious URLS for the latest in ransomware and threat intelligence. The Cloud Ticket Orchestrator (CTO) automatically creates service tickets from Netskope alerts within IT service management and collaboration tools, helping to automate response workflows.
The Cloud Risk Exchange (CRE) enables the exchange and normalization of risk ratings between security solutions, adaptive policy controls to support zero trust principles, and can automatically invoke CTO service tickets to trigger investigations. And the Cloud Log Shipper (CLS) experts Netskope logs to SIEMs and data lakes, smoothly enabling security operators with rich details of web and cloud activity.
Palo Alto Networks Prisma Cloud Code Security
The technology Palo Alto Networks acquired earlier this year from Bridgecrew contains instructions on how to build infrastructure to avoid problems in production. Once the offering is integrated into Prisma Cloud, the company said developers will be able to spot problems such as an open S3 bucket right in their IDE (integrated development environment) without even having to go into their CI/CD tools.
The integration of Bridgecrew and Prisma Cloud will alert developers to problems earlier in the life cycle before they enter production and will be generally available to customers starting in January 2022. With Prisma Cloud Code Security, infrastructure as code scanning and code fixes are embedded directly into developer tools across the development life cycle, meaning risk will be addressed earlier.
The technology can also spot if security groups are overly permissive in source code repositories such as GitHub or GitLab and let the developers know to ensure the issues aren’t replicated in production. Bridgecrew pioneered technology that allows for the scanning of code early in the development pipeline to ensure that there aren’t any problems during production, the Santa Clara, Calif.-based company said.
Varonis DatAdvantage Cloud
Varonis DatAdvantage Cloud was unveiled in May to visualize and prioritize security risk, allowing clients to see and prioritize their biggest cloud risks, proactively reduce their blast radius, and conduct faster cross-cloud investigations. It correlates identities with privileges and activities across cloud stores, including Amazon Web Services, Box, GitHub, Google Drive, Jira, Okta, Salesforce, Slack and Zoom.
DatAdvantage Cloud provides a clear view of permissions across an organization’s cloud services with recommendations to eliminate excessive, inappropriate, or unused privileges. It prevents cloud account takeovers, insider threats, and inadvertent policy violations with cross-cloud auditing and alerts on suspicious activity and policy violations, according to New York-based Varonis.
Cloud events can be normalized and enriched with DatAdvantage Cloud to allow security analysts to investigate incidents cross-cloud without having to craft complex, service-specific queries, Varonis said. DatAdvantage Cloud can also automatically link accounts across disparate cloud services to form a single identity while easily uncovering over-privileged shadow accounts both human and non-human.

Zscaler Workload Communications
Zscaler Workload Communications debuted in December to eliminate attack surfaces, prevent lateral threat movement, inhibit compromise of workloads, and stop data loss by extending zero trust security to workloads and applications hosted in public clouds. It also boosts multi-cloud workload connectivity by moving away from traditional IP-based routing and VPNs between cloud environments, Zscaler said.
The San Jose, Calif.-based company said the industry’s first zero trust for cloud workloads tool secures cloud-to-internet, cloud-to-cloud, cloud-to-data center, and intra-cloud communications. Acting as an intelligent switchboard, traffic is routed to the Zscaler platform where connections are brokered using business policies based on identity and context to connect workloads directly to other workloads.
Zscaler said its approach eliminates the attack surface by making workloads invisible to the internet, simplifies application connectivity by removing networking bottlenecks, and delivers strong application performance by reducing app-to-app latency. Zscaler said its new offering allows enterprises to secure all workload communications over any network, including internet, direct connect, and express route.